Microsoft Power Platform DLP Bypass Uncovered – Finding #4 – Unblockable connectors

Hello everyone! I’m Yuval Adler, Customer Success Director at Zenity.
I’m inviting you to read my blog series where I share new Microsoft Power Platform DLP Bypass findings we’ve uncovered.
Finding #4: Unblockable connectors
Microsoft Power Platform is a leading low-code/no-code platform that offers many capabilities for creating custom applications and automating workflows. After examining its security options, we have identified several limitations that could expose the organization to new security risks that administrators may not be aware of (check out the problem with enforcing DLP policies for pre-existing resources, and the issues around HTTP calls or using custom connectors).
Microsoft introduced Data Leak Prevention (DLP) policies to define the consumer connectors that specific business data can be shared with, and which connectors are blocked for usage – similar to an allow and block list. These connectors enable users to access data from these external systems and services within the Power Platform, making it possible to create workflows, automate processes, and build custom apps.
Although DLP has some capacity to distinguish between business and non-business connectors (see previous blogs to review several ways to bypass that), it may not be possible to completely block usage to all data through several connectors. There is a list of connectors in the DLP policy that by default are configured to be “Unblockable” which is an alarming discovery. This places administrators in a difficult situation, as they have limited control over how to restrict the use of several connectors that possess robust capabilities.
The following is a partial list of connectors that can’t be blocked by using DLP policies:
- PowerApps custom connectors
- Microsoft Dataverse
- SharePoint
- OneDrive for Business
- Dynamics 365
- Office 365
- Microsoft Teams
The connectors above have strong capabilities when it comes to interacting with sensitive files, confidential documents and proprietary information. The full list can be found on Power Platform Admin Center under the DLP configuration → Pre Built connectors → Non-business → filter by Blockable = no (screenshot below or in the docs here).
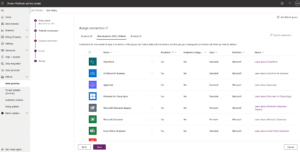
What’s the true impact of the discovery that these connectors can’t be configured? It means you can’t block their usage or limit it by allowing or denying endpoints/actions, and it means that these connectors will bypass any network restrictions and firewall policies, in order to allow the integration with external systems and services Power Platform needs.
One of Microsoft Power Platform’s biggest use cases is personal productivity. The platform is used by individuals who want to automate and streamline their work processes, and manage personal data in the sense of activities such as tracking expenses, creating task lists, and managing contacts, where the main goal is to increase efficiency and make better use of time.
The inability to properly set up connectors for accessing confidential and sensitive data, such as SharePoint or OneDrive, poses a significant challenge for LCNC administrators who aim to establish safeguards to ensure that Power Platform is solely used for personal productivity.
Because of that, users will continuously control the capability to access business data, placing the LCNC administrators in a position where they must carefully monitor the situation to prevent any data leaks or violations of permissions. The administrators are on their own, because Power Platform does not provide any tools to do this.
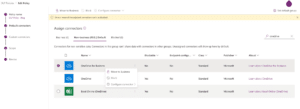
In the following demonstration I will take OneDrive as an example of how the lack of ability to block this connector can potentially cause data leakage where sensitive data is being exposed or shared with unauthorized parties. In the below, you can see the OneDrive for Business connector in the DLP policy’s connectors list. You can see that there is no option to block it or configure it (both options are grayed out).
As a user I have in my business OneDrive folder a confidential file under the name “Sensitive information” and I’ve created a flow which will use the OneDrive for Business connector to create a link which will expose this file to anyone who uses this link, with no need to authenticate or have specific permissions.
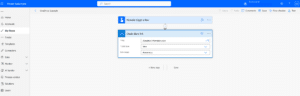
I was able to run the flow successfully.
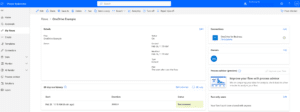
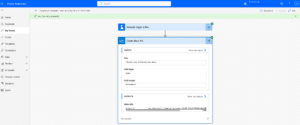
In the flow run here, I can see the URL to access the file, and can now share it with anyone I want. Without the need for a login, they can review the file and its content. Below, I opened the file with no user authentication (As you can see in the upper right side mentioned “sign-in” for login) and I was even able to download the file to my personal laptop.
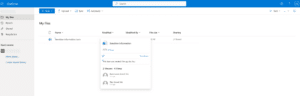
Next, you can see my business OneDrive folder where I can review who opened my doc and I see one guest viewed my file.
This is a very concerning example of how, by creating a simple flow, a user can expose the organization to major security risks. Just as concerning is the fact that administrators have no actual way to block it, or even monitor or have visibility into it.
It’s important for administrators to be aware of the capabilities of DLP and to establish appropriate controls and monitoring to prevent unauthorized access to sensitive data.
In order to address these security risks and provide our customers with more visibility, at Zenity we’ve added dedicated rules to our security rules set to monitor these scenarios, alert our customers of potential data leakages in their organization and provide them with the ability to automatically remediate any issues that arise.
To learn more about the security risks mentioned in this article or in the earlier articles in this series, feel free to reach out over email to yuvala@zenity.io and I’ll be happy to help! For the 5th and final installment of this blog series, click here, where we talk about parent and child flow execution.



