Retail/Manufacturing
Business-Led Innovation Transforms Retail & Manufacturing
Anyone can now build apps, automations, and copilots. Can security keep up?
The pROBLEM
Maintaining operations when everyone is a developer is no easy feat
With AI, low-code, and no-code tools, the supply chain gets even more complex
Data Leakage
Apps and automations require access to sensitive data to work but less technical users create less technically sound apps
Supply Chain Attacks
If one component is insecure or unpatched, lots of apps, automations, and copilots can become immediately impacted
Shadow App Development
With IT no longer needed to build powerful business apps, visibility over who creates what is decreased
Vulnerability Management
With thousands of apps to manage, security teams must demonstrate that they know how to identify and mitigate vulnerabilities
The solution
Unleash citizen development and Generative AI throughout the enterprise
The Zenity security governance platform empowers retail and manufacturing companies to enable business users to be productive and efficient
Real-time Inventory
Automatically identify all apps, automations, flows, and bots created across various AI and low-code platforms
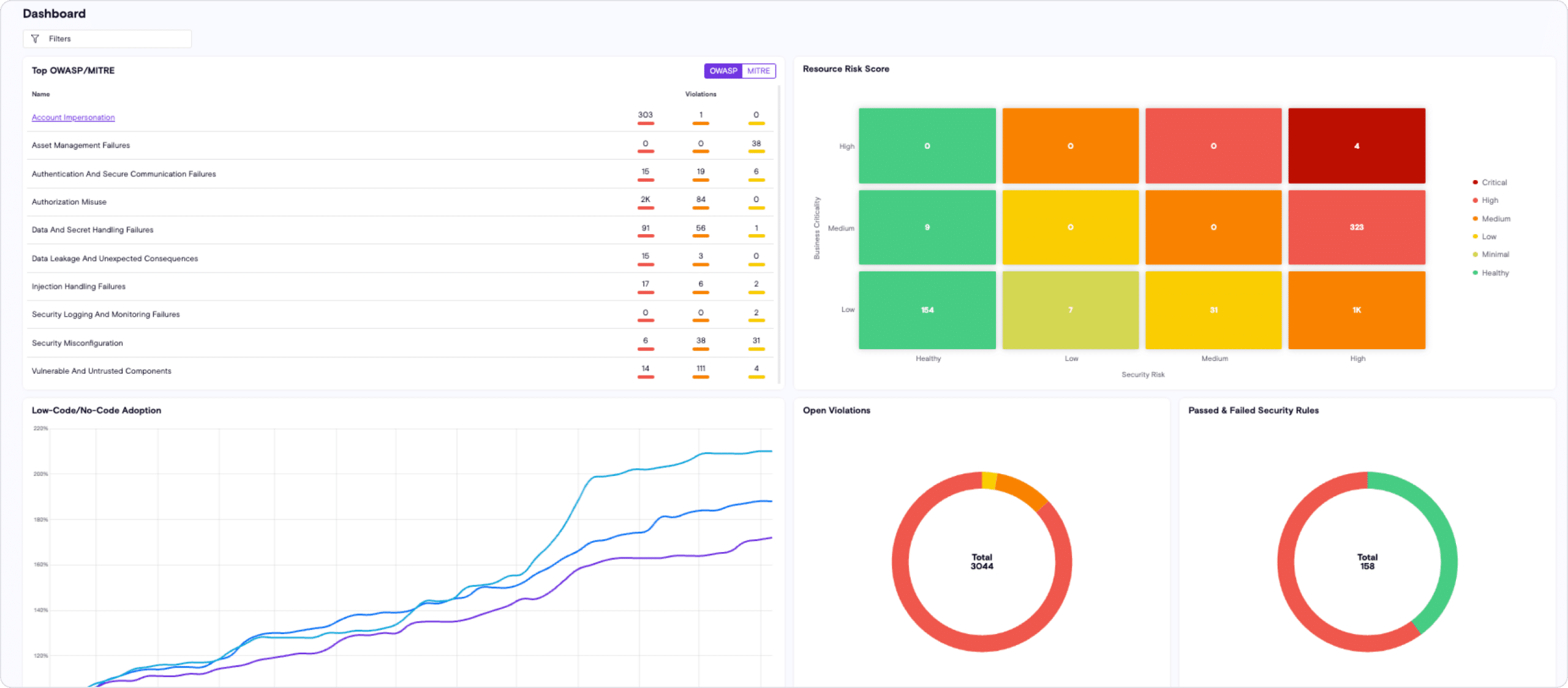
Risk and Hygiene Assessment
Assess each resource for vulnerabilities, including third-party components, and map them to popular security frameworks
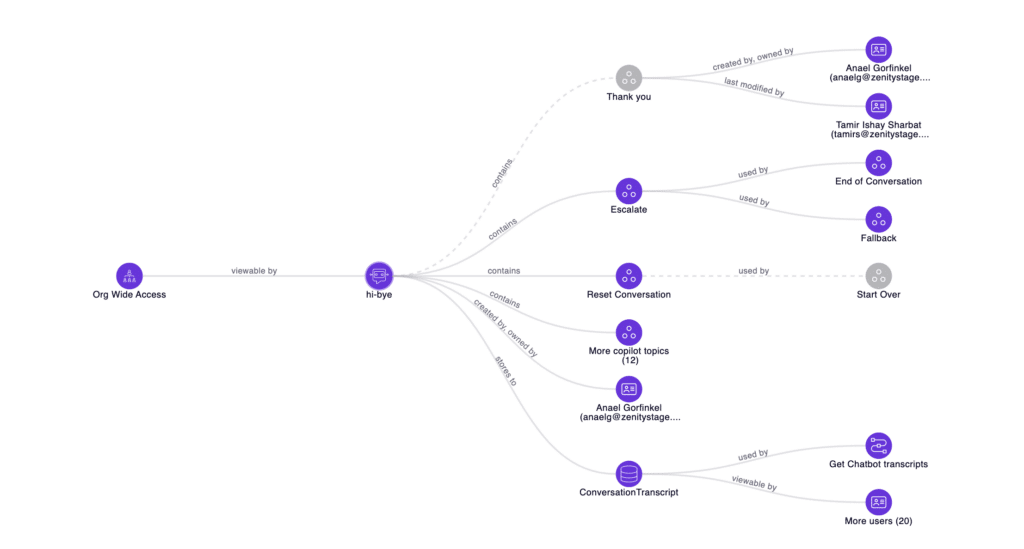
Implement Playbooks and Policies
As risks are identified, empower security teams with the ability to enforce guardrails for secure development
Enable secure, business-led innovation
With Zenity, retail and manufacturing enterprises can ensure that as people get closer to AI, low-code, and no-code development, that the apps and automations are secure
Minimize Data Leakage
Prevent apps and AI copilots from leaking data outside the corporate boundaries
Enhance Supply Chain Security
Empower business users with the knowledge that security can spot any risky components being built into apps and copilots
Eliminate Shadow App Development
Identify and assess each individual app, automation, and copilot that is created by citizen developers
Reduce Noise and Respond
Prioritize what matters most from a security and business criticality perspective and implement autonomous guardrails for secure development
Securing my LCNC – Where to Start?

Want to learn more?
We’d love to hear from you and talk about all the latest updates in the world of low-code, no-code, and Al led development