Security & Governance that Unlocks Innovation
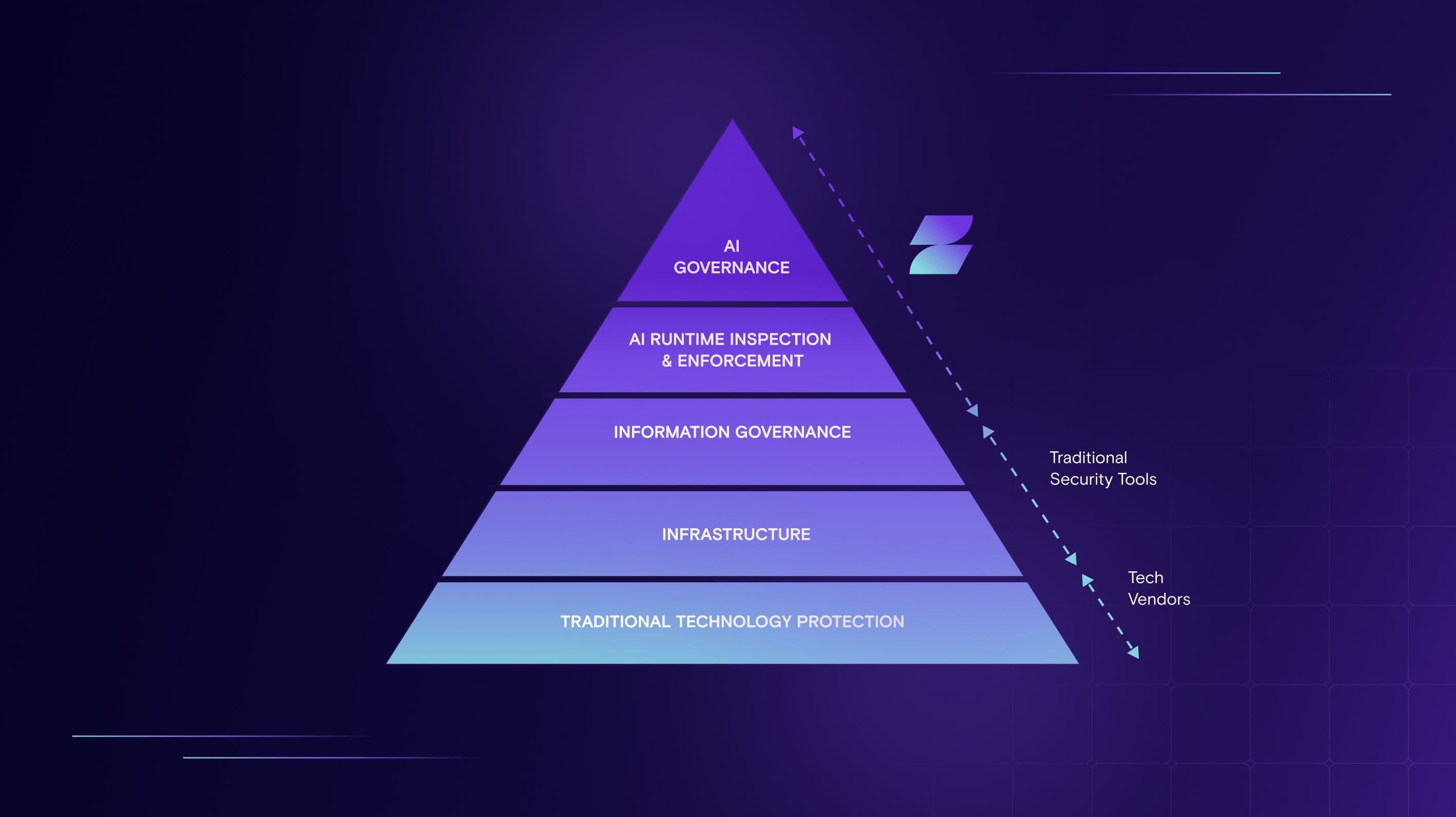
Security teams are used to being brought in late and asked to clean up risks they didn’t create. With Zenity, security takes the lead from the start, shaping AI Agent adoption across the enterprise. Zenity delivers in-depth security through a unified, end-to-end platform that spans buildtime to runtime. With deep expertise in low-code/no-code security, Zenity brings a unique, agent-centric approach - giving teams the visibility to understand how agents behave, the guardrails to prevent missteps, and the confidence to respond when risks emerge.
Embrace AI Agents
Secure AI Agents from buildtime to runtime, identifying misconfigurations early and detecting risky behavior in real time
Govern AI Agents
Ensure safe and responsible use by governing how AI Agents are built, how they behave, and how they interact with your enterprise
Secure AI Agents
Unified observability, posture management, and detection and response - all in one comprehensive end-to-end platform to help manage risks and threats at scale