Salesforce
Security and Governance for Salesforce
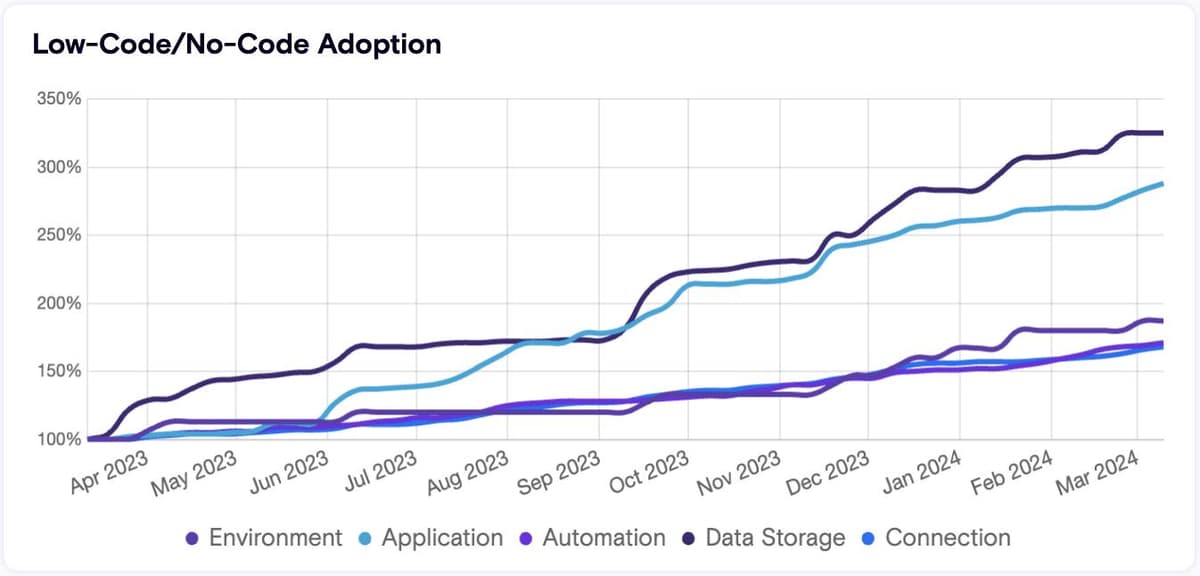
Salesforce offers a variety of agentic capabilities and ways for anyone to build and use AI Agents

As Salesforce Grows, What Security Risks Emerge?
Salesforce has made an aggressive push to put AI Agents into the hands of everyone, even enabling anyone to build custom agents with native capabilities from the CRM leader.
Speed of Development
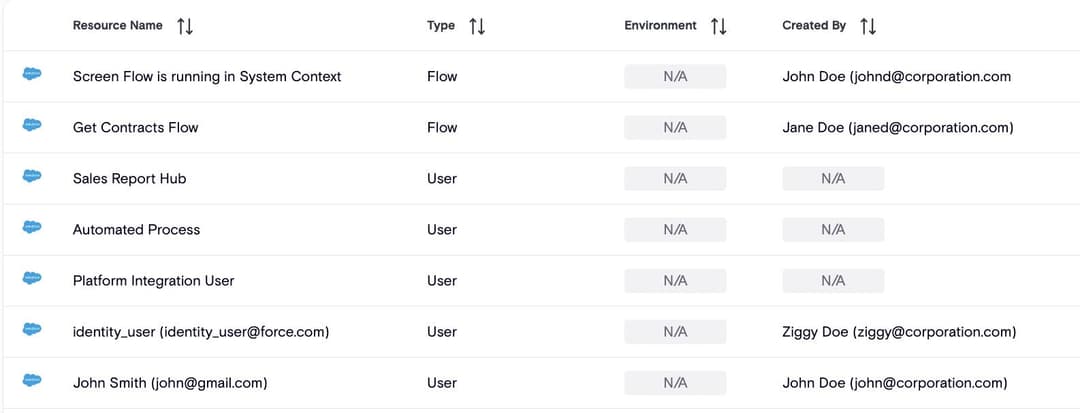
With Agentforce, anyone can create powerful AI Agents that interact with sensitive corporate and customer data, resulting in shadow development
Data Leakage Risks
Agents and other apps and reports built in Salesforce push and pull lots of sensitive data, creating easy ways for data to leak
Empower Everyone to Build Useful Agents, Apps, and Automations
Zenity’s security governance platform makes it so that as business users adopt and build on Agentforce, Lightning App and Flow Builder, MuleSoft, IDEs, Apex, and Einstein AI that the ensuring agents, apps, and reports are not leaking data
Confidently Secure Salesforce AI Agents & Low-Code Apps
With Zenity, professional and citizen developers can embrace the power of AI to get more done and process more data while maintaining security and governance
Secure Your Agents
We’d love to chat with you about how your team can secure and govern AI Agents everywhere.
Get a Demo