Generative AI
Unlock the Value of AI Securely Throughout Your Enterprise
Gen AI has changed the game, bringing people closer than ever to the cutting edge… but also closer to data leaks

Harnessing copilots means governing them
Zenity helps avoid common security and compliance risks stemming from enterprise copilots like prompt injection, RAG poisoning, and copilot data leakage
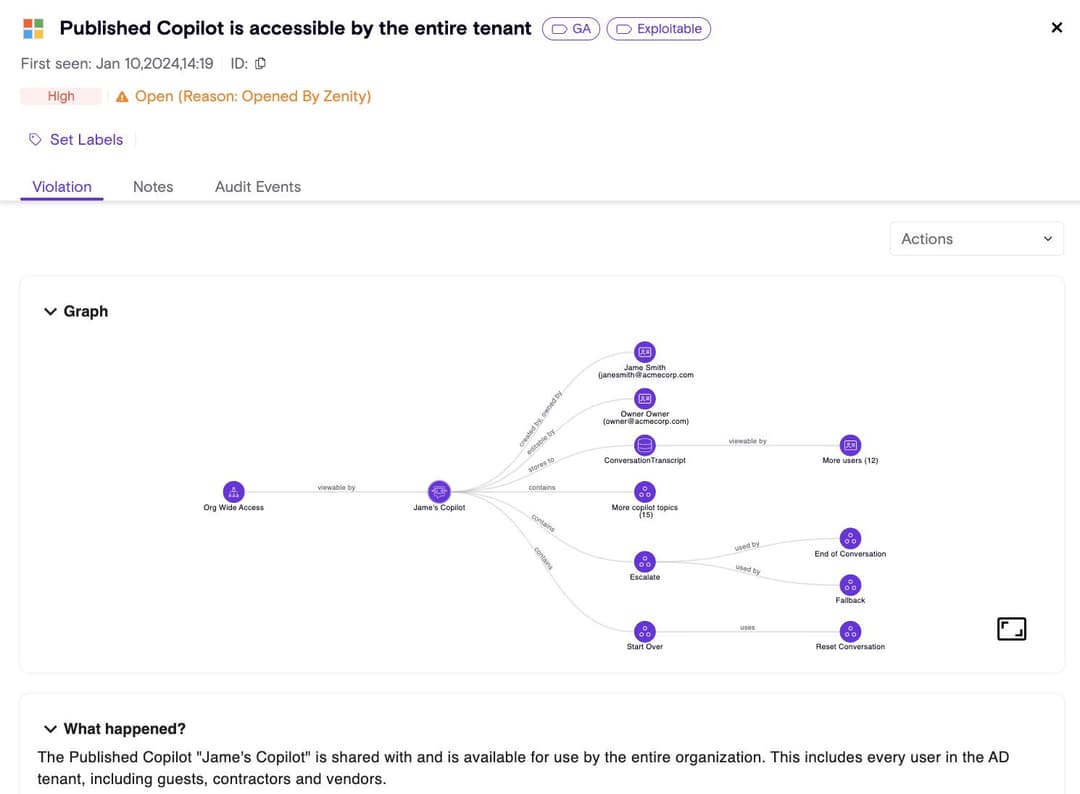
Lack of Visibility
Copilots are often a black box, where data is processed, stored, and remitted outside of your control, and anyone now able to build their own copilots
Insecure by Design
Copilots are often built with poor authentication mechanisms, overshare data (including transcripts), and are overshared to trusted and untrusted users
AI changes everything. Except the need for security
Zenity provides full visibility and control across enterprise copilots and AI apps, preventing data leakage, RAG poisoning, and prompt injection attacks
Secure AI Throughout the Enterprise
As users of all technical backgrounds lean on Al to get more done, Zenity makes sure they are secure
Continous Discovery
Catalogue all AI apps, copilots, and plugins that are created and used throughout the enterprise
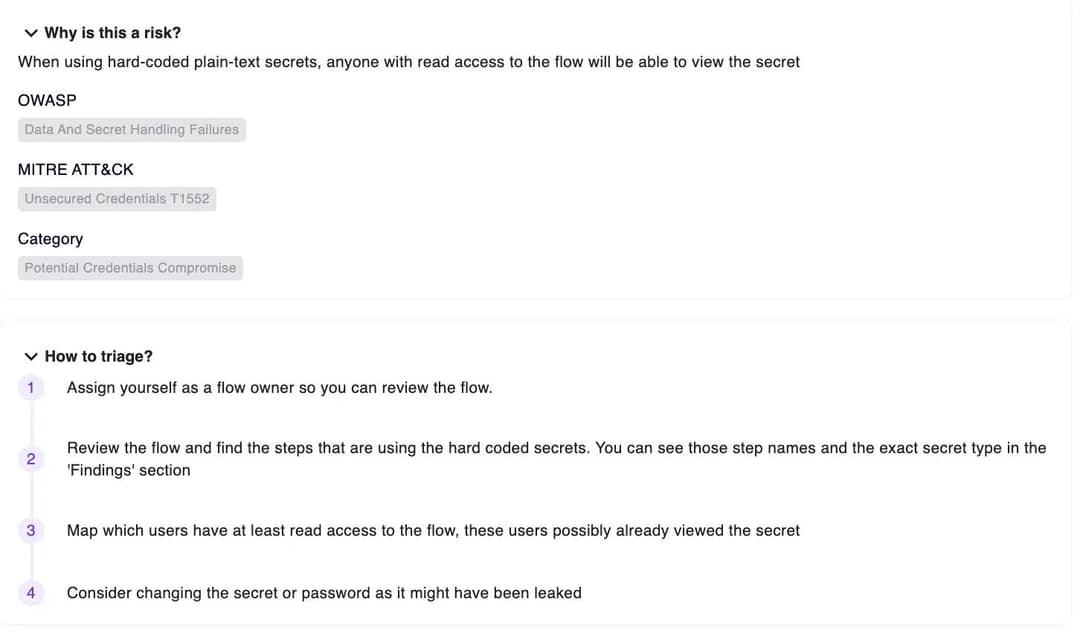
Detect and Mitigate Vulns
Only Zenity can provide comprehensive risk assessment using deep business context for all AI apps and copilots
Making Sense of AI in Cybersecurity
In this blog, we’ll make some distinctions between the different types of AI security to help you make sense of it all so you can improve security without hindering business processes.

Secure Your Agents
We’d love to chat with you about how your team can secure and govern AI Agents everywhere.
Get a Demo