Microsoft 365 Copilot
Securely Unlock Microsoft 365 Copilot
Zenity helps protect against direct and indirect prompt injection, data leakage, and jailbreak attempts.
Real-Time Data Means Real-Time Issues
As enterprises adopt Microsoft 365 Copilot, bad actors can easily manipulate Agentic AI to gain full control over your enterprise
Understanding Curious AI
Enterprises need to see not only user/agent interactions, but the logic behind why Agentic AI does what it does
RAG Poisoning
As 365 Copilot retrieves data, hackers can take full control of what data and files end users see with hidden instructions
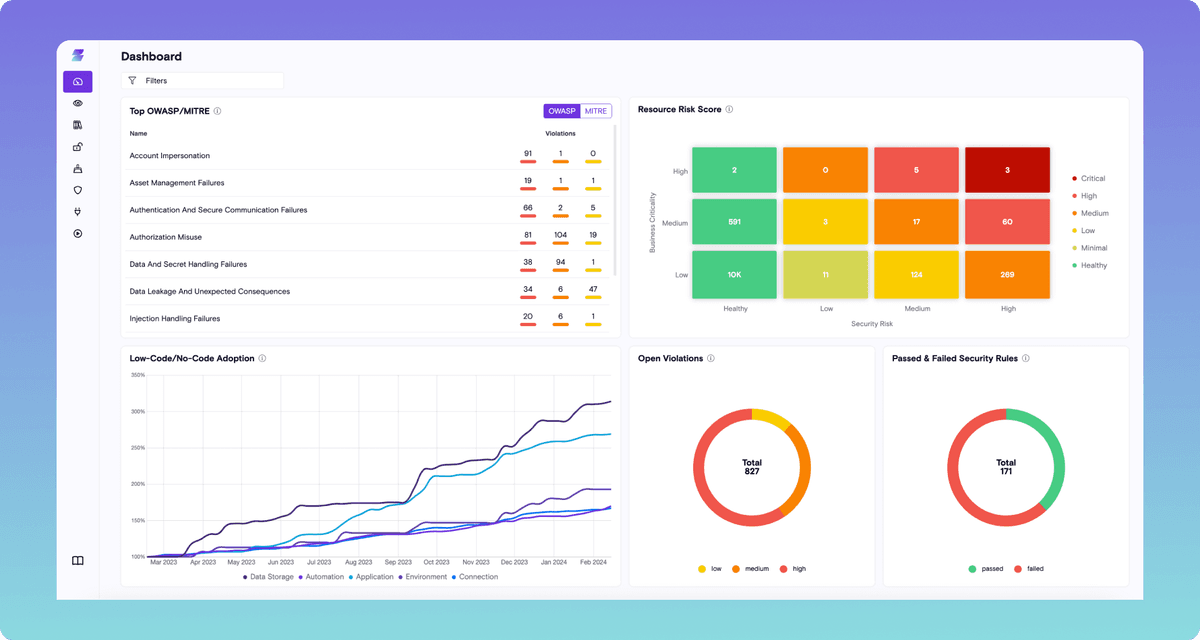
The Zenity AI Trust Layer for Microsoft 365 Copilot
Zenity secures Microsoft 365 Copilot from buildtime to runtime with real time vulnerability and threat detection, continuous monitoring, embedded control, and automated remediation.
Enable the Business. Unleash Microsoft 365 Copilot
Zenity provides the only agentless AI security solution on the market that helps to secure and govern the end-to-end use of Microsoft 365 Copilot
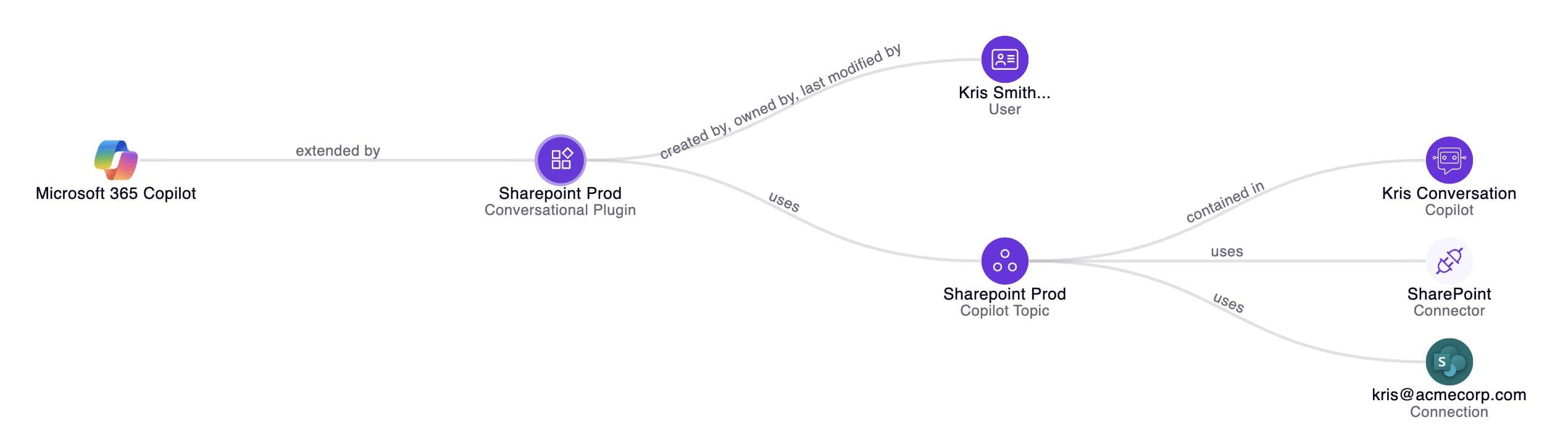
AgentFlayer: The 0Click Threat to AI Assistants & Agents
Zenity Labs revealed AgentFlayer, a set of 0click and 1click exploit chains that let attackers hijack enterprise AI agents and assistants - often without any user action.
For Microsoft 365 Copilot, our simulation showed how a single malicious Teams message or infected document could seize control, exfiltrate sensitive chats, and manipulate responses from within trusted channels.
See the full research for complete attack chains against the most popular enterprise AI platforms, including ChatGPT, Microsoft Copilot Studio, Salesforce Einstein, and others.

Secure Your Agents
We’d love to chat with you about how your team can secure and govern AI Agents everywhere.
Get a Demo