Power Platform
Leverage Power Platform to the Max with Strong Security
Zenity helps ensure that apps, automations, flows, and reports that are built across Power Platform (PowerApps, PowerAutomate, PowerBI) are secure and in line with corporate policy

Taking Security and Governance to the Next Level
Zenity brings deep security and governance to Power Platform to enable enterprises to take advantage of the powerful suite of development tools
Shared Responsibility
Much like the shared responsibility of the public cloud, Microsoft secures Power Platform services, but not your data or the resources built on top
CoE is just a Start
The massive scale of citizen development introduces vulnerabilities and misconfigurations that lead to data leakage
Embrace Citizen Development with Power Platform
Power Platform offers lots of exciting capabilities to business users, but too many security teams can’t keep up. Zenity can help
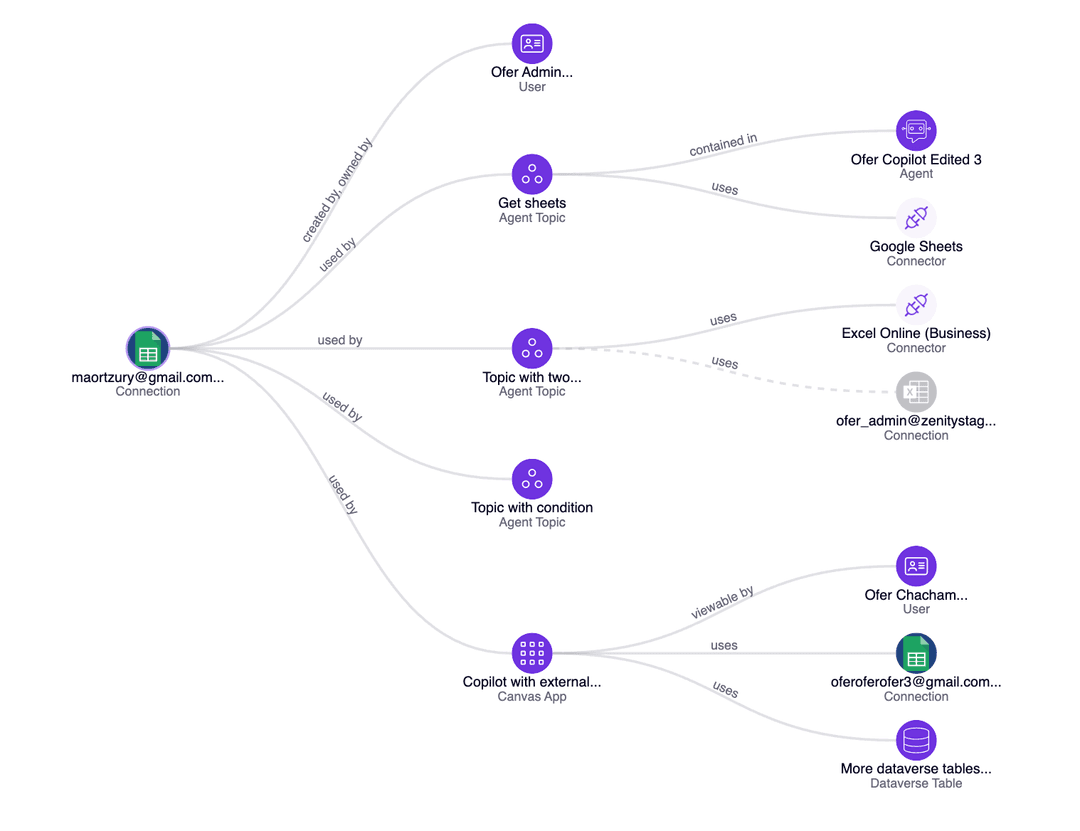
Secure Low-Code Development with Zenity
Zenity provides deep, business-level logic and actionable insights to ensure Power Platform is properly secured and governed

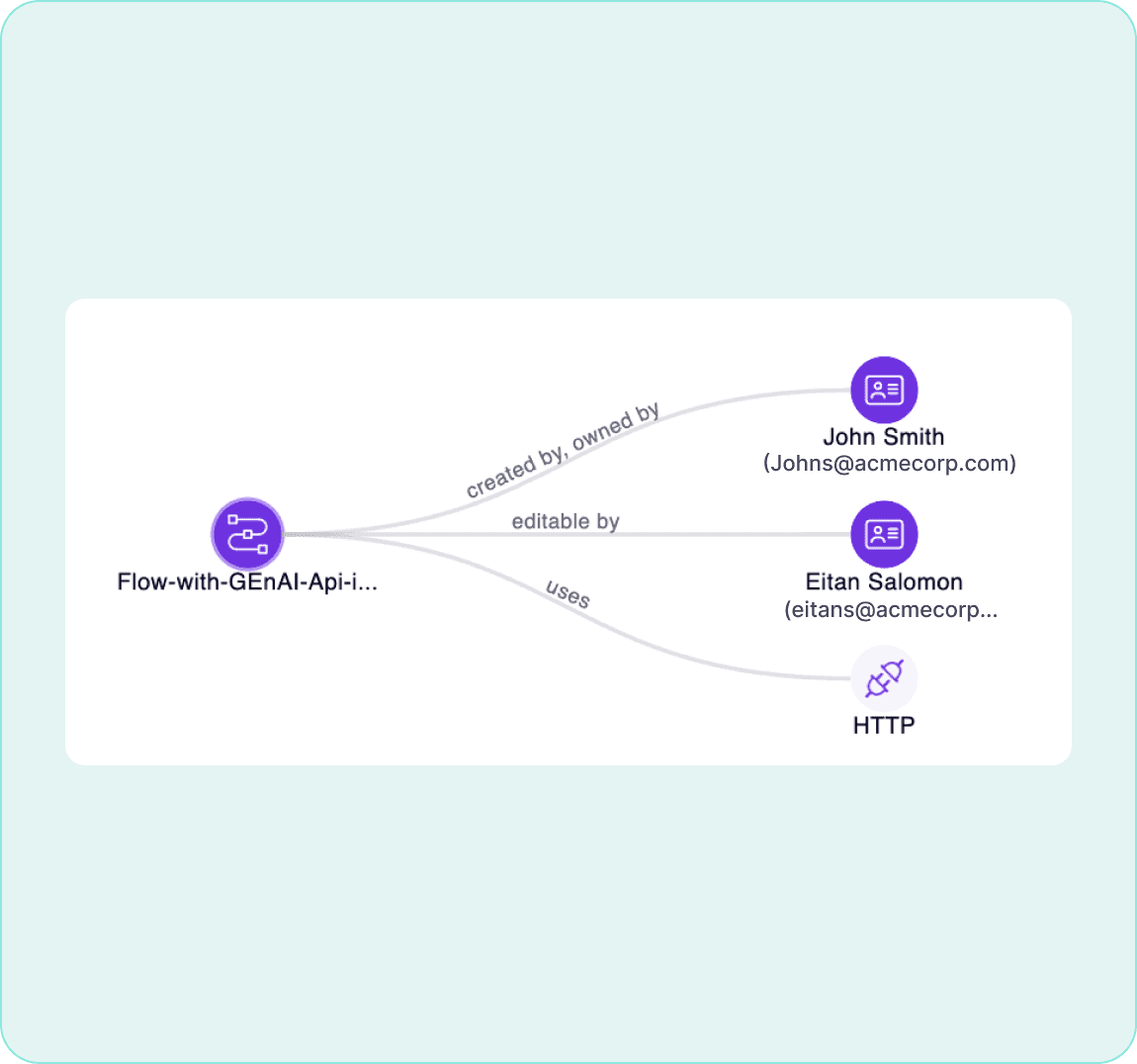
Secure Your Agents
We’d love to chat with you about how your team can secure and govern AI Agents everywhere.
Get a Demo