Retail/Manufacturing
Business-Led Innovation Transforms Retail & Manufacturing
Anyone can now build apps, automations, and agents. Can security keep up?
Maintaining Operations When Everyone is a Developer is No Easy Feat
With AI, low-code, and no-code tools, the supply chain gets even more complex
Data Leakage
Apps and automations require access to sensitive data to work but less technical users create less technically sound apps
Supply Chain Attacks
If one component is insecure or unpatched, lots of apps, automations, and copilots can become immediately impacted
Embrace AI Agents Throughout the Enterprise
The Zenity security governance platform empowers retail and manufacturing companies to enable business users to be productive and efficient
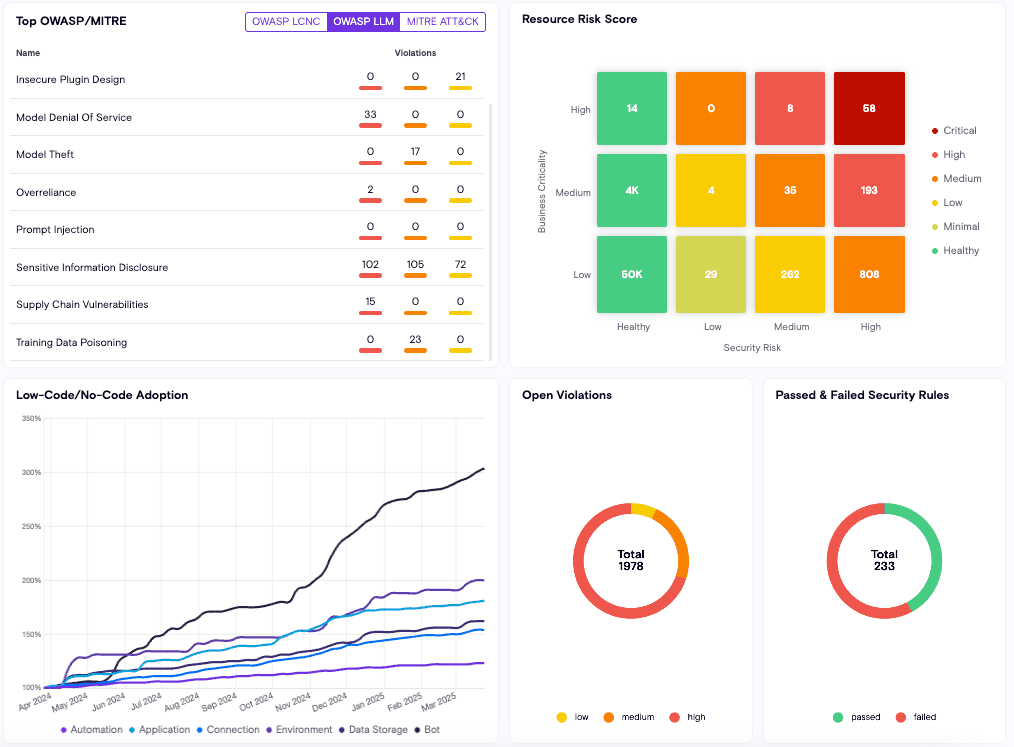
Enable secure, business-led innovation
With Zenity, retail and manufacturing enterprises can ensure that as people get closer to AI, low-code, and no-code development, that the apps and automations are secure
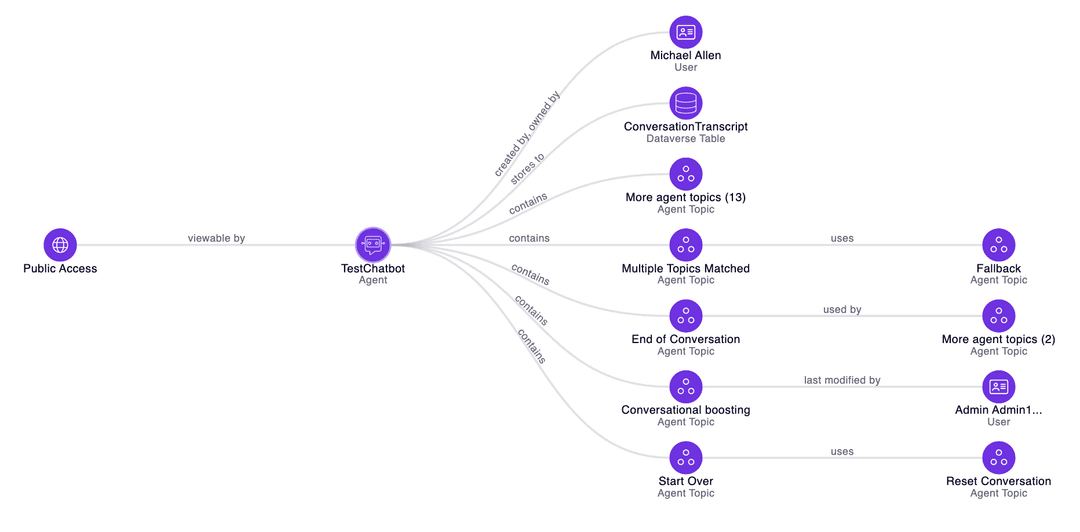
Minimize Data Leakage
Prevent AI agents and low-code apps from leaking data outside the corporate boundary
Enhance Supply Chain Security
Empower business users with the knowledge that security can spot any risky components being built into apps and copilots
Securing my LCNC – Where to Start?
Based on our experience working with many of the world’s largest and most complex organizations, we’ve compiled the three main pillars organizations need to enact when it comes to securing and governing low-code/no-code development.

Secure Your Agents
We’d love to chat with you about how your team can secure and govern AI Agents everywhere.
Get a Demo