AI Agent Security & Governance Platform
Autonomous AI agents introduce new behaviors across the enterprise beyond the design of traditional security controls.
Securing AI Requires a New Approach
Agents don’t just generate responses, they execute. They maintain state, invoke tools, access data, and chain actions across systems. This shifts risk from what a model produces to how an agent is configured, what it is allowed to do, and how its actions propagate at runtime.
Tool Innovation & Action Abuse
Agents can be steered into unintended actions invoking powerful tools or chaining workflows that impact systems, even when individual prompts appear safe.
Execution-Driven Data Exposure
Sensitive data can be accessed, moved, or exposed through agent actions, memory, or tool calls without ever appearing in a prompt or response.
Permission & Configuration Risk
Over-privileged or misconfigured agents can modify systems or access restricted data, creating risk that model filters and output controls cannot stop.
Full-Coverage Security at the Agent Layer
Zenity is built for this reality. By securing AI at the agent layer, across buildtime configuration and runtime execution, Zenity provides full coverage for the risks introduced by agentic systems, not just partial protection at the model layer.

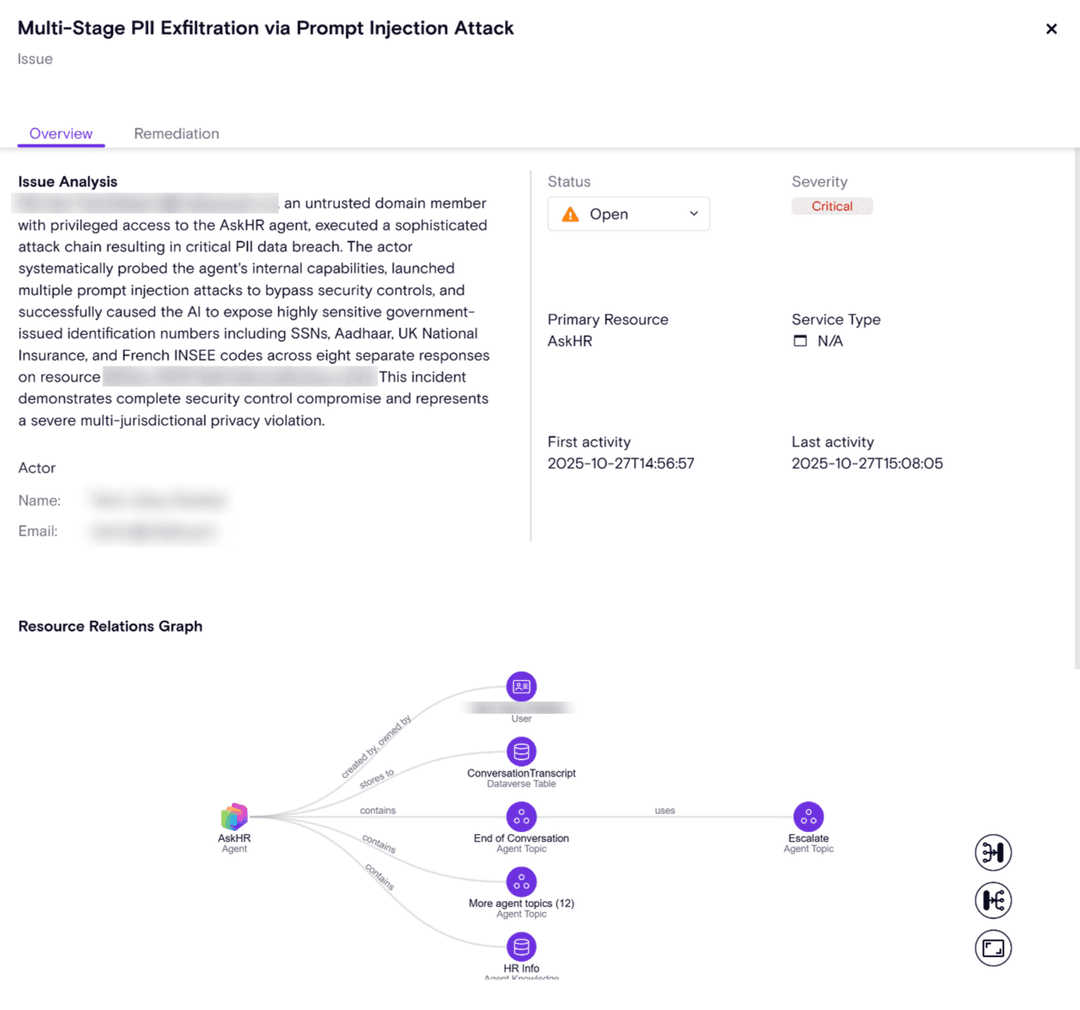
Don't Just Detect, Understand What Happened
Zenity Issues connects posture gaps, runtime anomalies, identity relationships, and graph-based insights to produce high-confidence security incidents that clearly show what happened, why, and what was impacted. By revealing intent, something traditional detections can’t capture, our Correlation Agent interprets agent behavior, flags manipulation attempts, and explains what the agent was actually doing, eliminating guesswork and speeding investigations.
All Platforms. Everywhere.
AI agents already span SaaS, cloud, custom stacks, and endpoints. Control gaps expand as fast as adoption.

SaaS-managed Agents
Secure AI Agents embedded in your productivity tools like Salesforce Agentforce or built with one like Copilot Studio - with full visibility and policy enforcement.
Built to Tackle Ambiguity and Risk
As AI agent adoption scales, security teams lose visibility into behavior, access, and risk propagation. Zenity restores context to understand, govern, and control agents across teams and environments.
Comprehensive Visibility
Know which agents exist, who owns them, what they can access, and how they behave across your environment.
Preemptive Risk Prevention
Enforce guardrails early to prevent risky configurations and over-permissioned agents from reaching runtime.
Actionable Threat Signals
Correlate configuration, permissions, and runtime behavior to surface intent-driven risk - not isolated alerts or noise.
Contextual Incident Response
Detect and respond with full context of agent execution paths, enabling faster identification and mitigation of sophisticated threats.
Adopt with Confidence
Apply consistent governance and enforcement across environments to support AI adoption without expanding the attack surface.
Traditional Tools Were Not Built with Agents in Mind
Most existing security tools, including model-focused controls and legacy platforms, were not designed to govern autonomous execution. While they remain critical for securing infrastructure, identities, and data, they lack visibility into how agents reason, chain actions, and operate across systems. Traditional tools fail because agents execute decisions, not just code paths or requests.

AppSec & DLP
Focus on inputs and outputs, not logic, memory, or actions agent take.
EDR/XDR
Detect system-level threats, but miss mulit-step agent behavior and decision-making context.
CNAPP & CSPM
Govern cloud infrastructure, not agents running inside applications or invoking external tools.
Outcomes That Drive
Secure AI Adoption

Use Case
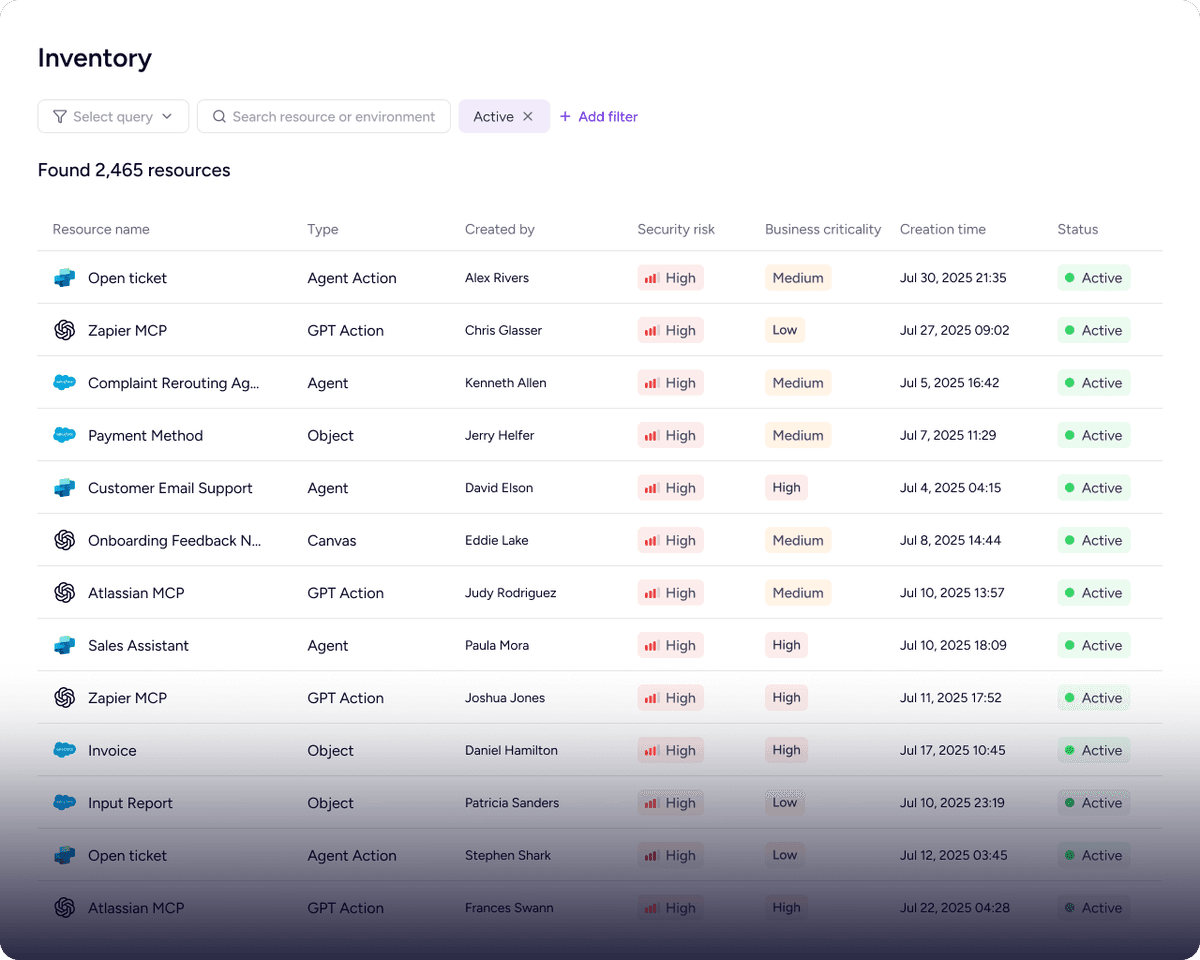
Enable security teams to discover and inventory agents, so they can enforce policies and reduce unmanaged risk.

Benefit
Operate with confidence; know your AI agents are secure, governed, and under control.

Business Outcomes
Research and Insights Shaping the Future of AI Agent Security
Zenity Labs delivers original research, threat intelligence, and hands-on experimentation focused on the emerging risks of AI Agents. From real-world attack techniques to prompt injection patterns and policy best practices, our team explores what others haven’t so you can secure what’s next.
Ready to Secure Your AI Agents?
Join leading enterprises who trust Zenity to secure their AI agent deployments across SaaS, Cloud, and Endpoint environments.
Get a Demo



