AI Security Posture Management
Secure AI Agents Before They Run
Enforces guardrails for agent configuration, permissions, and integrations managing vulnerabilities before agents ever run.
Recognized by







































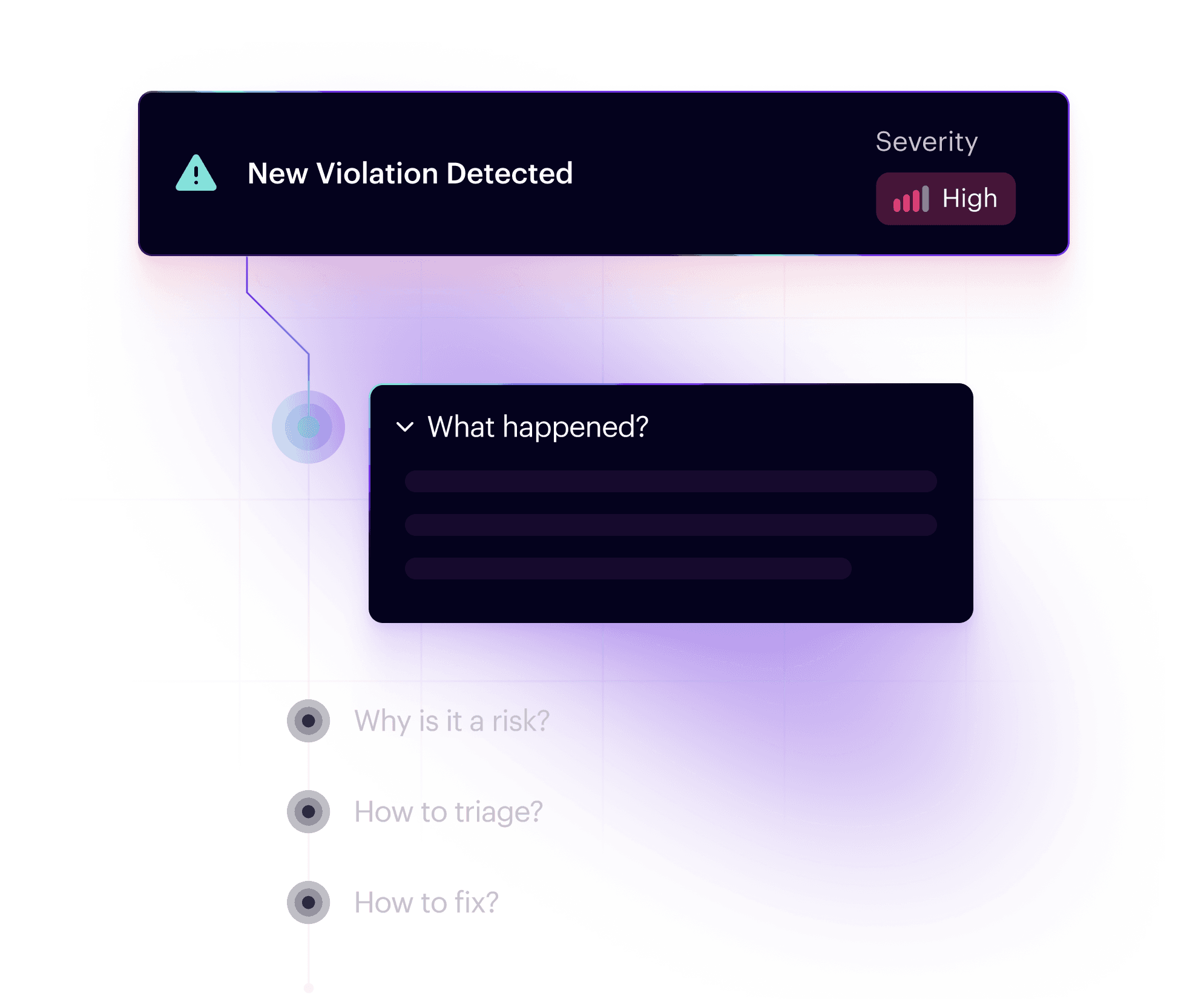
AI Agents Are Configured Without Guardrails
AI agents are often enabled and configured without consistent security standards.
Zenity AI Security Posture Management (AISPM) capabilities are purpose-built to govern how agents are configured. It discovers agents across environments, evaluates configuration and permission risk, and enforces secure-by-design guardrails enabling safe AI adoption without slowing teams down.

Prevent Agent Risk Before Execution
AISPM enables security teams to prevent agent risk at configuration. By evaluating permissions, integrations, and constraints early teams can apply guardrails consistently across embedded, custom, and endpoint agents.
Evaluate every stage
Review agent configurations, permissions, memory access, knowledge, instructions, actions, MCPs and tool integrations across the entire agent lifecycle.
Correlate risks quickly
Leverage unified platform intelligence from Observability and AIDR to correlate build-time risks with runtime behavior for rapid, precise triage.
Monitor risk & compliance continuously
Automate policy enforcement aligned with OWASP LLM Top 10, MITRE ATLAS, NIST AI RMF, and industry-specific regulations.
Risk Assessment Built for AI Agents

Secure AI Agent Configuration Across the Enterprise
Zenity enables security teams to apply consistent guardrails across all types of AI agents. Whether agents are embedded in SaaS platforms, custom-built for internal workflows, or running on endpoints, Zenity ensures they are configured safely before they operate.
ChatGPT Security
Comprehensive posture assessment of ChatGPT Enterprise and connected GPTs, evaluation of data access permissions across integrated SaaS apps, and continuous monitoring of agent memory, tool usage, and configuration changes.
Salesforce Agentforce Security
Complete security posture evaluation for customer data access, financial record handling, and integration with external systems.
Microsoft 365 Copilot Security
Comprehensive posture assessment of Copilot Studio agents and permission evaluation.
Shadow Agent Governance
Discovery and comprehensive risk assessment of unauthorized agents across business units.
Trusted by Forward-Looking Security Leaders
“With Zenity we were able to build a program to remediate existing vulnerabilities with a product that relies on self service and auto-fix so we can scale.”
Existing vulnerabilities remediated within 4 months with 2 FTEs
Tenant grew over 12 months
“We needed a way to partner with the business. Zenity gives us confidence to continue enabling our employees to innovate with AI Agents and applications.”
People developing these systems are not professional developers
Instances of agents and apps that were shared across the entire org
"Zenity provided a preventative layer to proactively reduce security violations of our Agentic AI use. As a result, we saw tremendous growth in cross-departmental adoption of AI Agents."
Reduction in security violations
High-risk violations automatically remediated
"With Zenity, we identified and managed risks from a huge attack surface containing over-shared resources that had access to sensitive data, DLP bypass routes, and misconfigured AI Agents."
Risk reduction across the tenant containing 150k+ total resources
Growth in agent, app, and automation volume
“With Zenity we were able to build a program to remediate existing vulnerabilities with a product that relies on self service and auto-fix so we can scale.”
Existing vulnerabilities remediated within 4 months with 2 FTEs
Tenant grew over 12 months
“We needed a way to partner with the business. Zenity gives us confidence to continue enabling our employees to innovate with AI Agents and applications.”
People developing these systems are not professional developers
Instances of agents and apps that were shared across the entire org
"Zenity provided a preventative layer to proactively reduce security violations of our Agentic AI use. As a result, we saw tremendous growth in cross-departmental adoption of AI Agents."
Reduction in security violations
High-risk violations automatically remediated
"With Zenity, we identified and managed risks from a huge attack surface containing over-shared resources that had access to sensitive data, DLP bypass routes, and misconfigured AI Agents."
Risk reduction across the tenant containing 150k+ total resources
Growth in agent, app, and automation volume
“With Zenity we were able to build a program to remediate existing vulnerabilities with a product that relies on self service and auto-fix so we can scale.”
Existing vulnerabilities remediated within 4 months with 2 FTEs
Tenant grew over 12 months
“We needed a way to partner with the business. Zenity gives us confidence to continue enabling our employees to innovate with AI Agents and applications.”
People developing these systems are not professional developers
Instances of agents and apps that were shared across the entire org
"Zenity provided a preventative layer to proactively reduce security violations of our Agentic AI use. As a result, we saw tremendous growth in cross-departmental adoption of AI Agents."
Reduction in security violations
High-risk violations automatically remediated
"With Zenity, we identified and managed risks from a huge attack surface containing over-shared resources that had access to sensitive data, DLP bypass routes, and misconfigured AI Agents."
Risk reduction across the tenant containing 150k+ total resources
Growth in agent, app, and automation volume
Analyst Recognition & Research Coverage
Start Securing Your
AI Agents Today
Your AI is already live. Is your security catching up?Zenity brings observability, enforcement, and protection under one roof.
Get a Demo