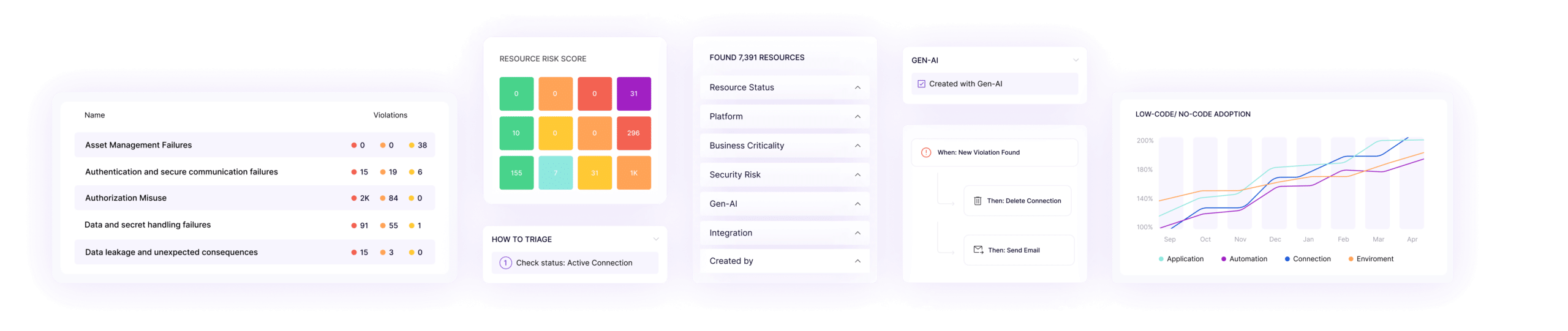
Monitoring & Profiling
- Real-time and ongoing observability to catalogue all AI Agents and low-code apps used across the enterprise
- Understand all topics, actions, and triggers for each AI Agent
- Monitor all interactions and corresponding actions that AI Agents take
- Create a baseline for normal activity to help with anomaly detection
Detection Response (AIDR)
- Identify key indicators of compromise correlated to external attackers, trusted insiders, or curious AI
- Detect direct and indirect prompt injection attacks, least privilege violations, hidden instructions, and more
- Automated responses to stop threats in their tracks
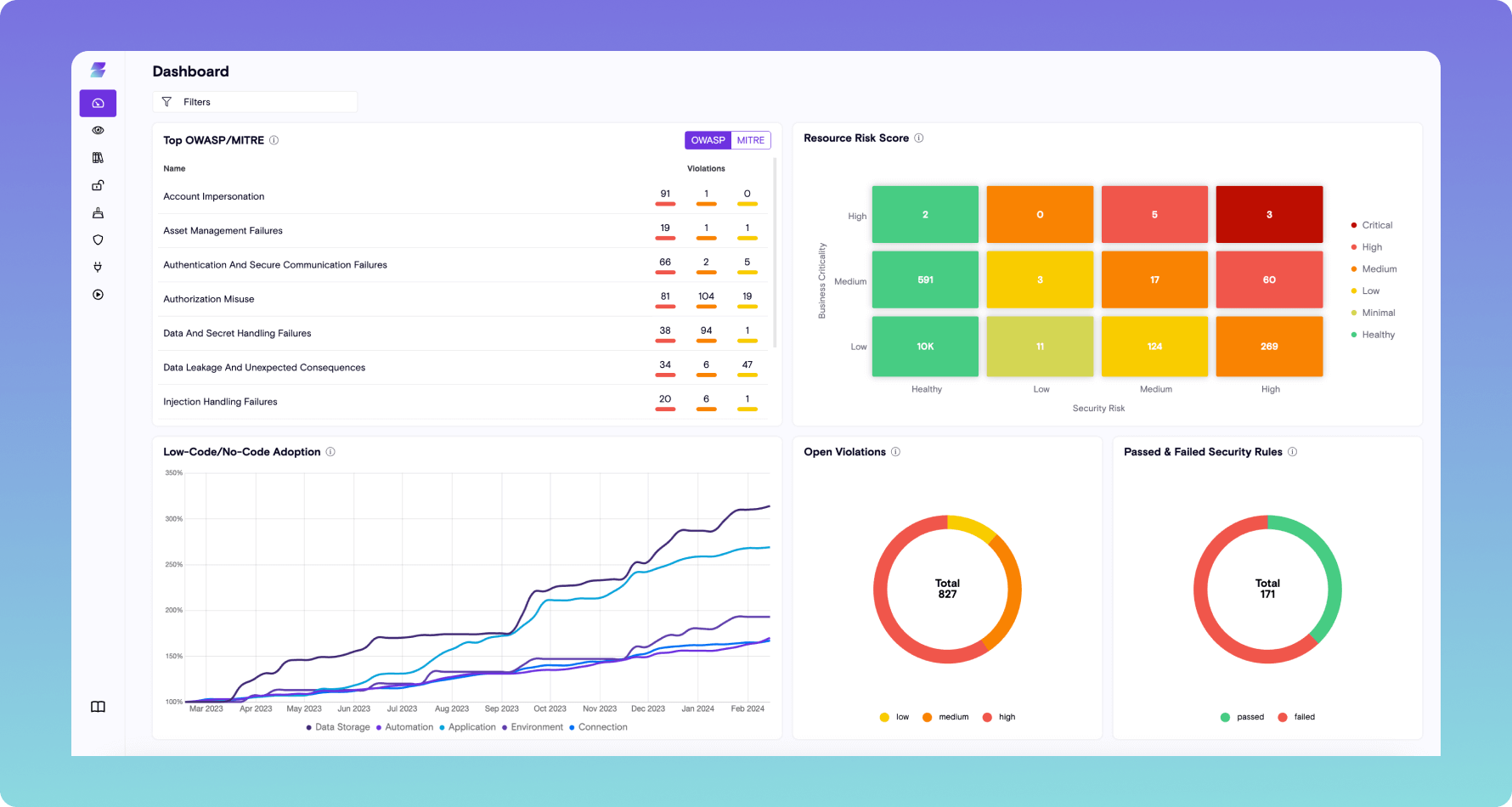
Risk Prevention
- Proactively reduce risk as AI Agents are adopted in the enterprise
- Prevent AI Agents and low-code apps from turning into phishing campaigns, remote takeover, and agent jailbreaks
- Works in tandem with native tooling, i.e. Microsoft Purview, to autonomously set enforcement controls when risks are detected to prevent further damage and future risks from emerging
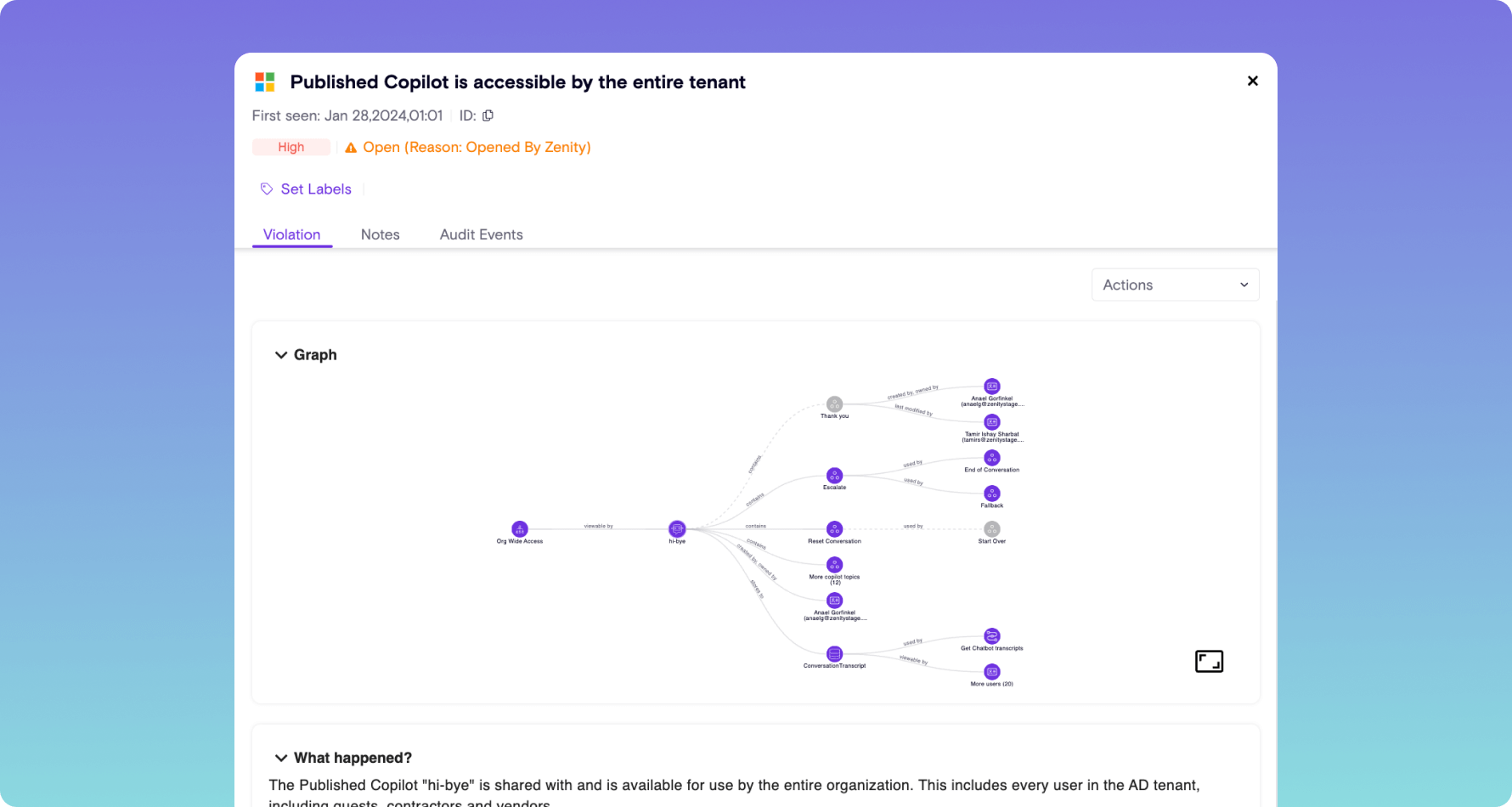
Security Posture Management (AISPM)
- Establish how AI Agents and low-code apps are being built, including deep knowledge of their components, topics, actions
- Ensure business users are not violating least privilege or leaking data with AI Agents and apps they build using low-code platforms
- Identify and manage risks that stem from common misconfigurations like least privilege violations, poor authentication, exposed secrets, over-sharing of sensitive data, and more