Microsoft Power Pages: Low-code Misconfiguration Remains a Top Security Risk
Power Pages = Portal Apps + Security?
Last week Dark Reading released an enterprise application security survey which raised serious concerns by IT and security teams Last week, Microsoft announced a new low-code application service called Power Pages, the fifth service joining the Power Platform.
Whether you’re a low-code maker or professional developer, this low-code, scalable, and secure solution empowers you to build business-centric websites quickly and easily.
Careful reading brings out two main points repeated throughout the release by Microsoft: security and ease-of-use. I will focus on the former.
Take a look at this excerpt from the announcement:
Securely collect and share business information with site visitors using Microsoft Dataverse, a smart, secure, and scalable low-code data platform. Power Pages runs on Microsoft Azure and connects with Dataverse to provide critical security capabilities that include advanced encryption, rich role-based access controls (RBAC), and support for Microsoft Azure Front Door and other web application firewalls. Microsoft Azure DDoS Protection addresses top web security vulnerabilities.
The message is repeated in image form:

Power Pages’ messaging is all about security
But what is Power Pages used for?
״For years, Power Apps portals have offered users an end-to-end experience to create external portals quickly and confidently, and customize them with pages, layouts, and content. As a new, standalone product, Power Pages empowers anyone, regardless of their technical background, with an effective platform to create data-powered, modern, and secure websites.״
Power Pages is an evolution of Portal Apps, Microsoft’s low-code solution to build external facing web applications. Security is a critical aspect of this evolution.
Regain confidence in Microsoft low-code application platform
There’s a good reason why the focus is on security. A little less than a year ago, security researchers found a major data leak stemming from insecure Portal Apps default configuration. In short, Portal Apps were generated by default with an API endpoint allowing anonymous access to application data.
Microsoft was quick to react to that incident, changing the insecure default, and even going so far as blocking APIs and asking customers to explicitly reopen them, as verified by the Zenity research team.
However, this wasn’t enough for all customers. Some got scared and turned off Portal Apps entirely. That makes sense, since Power Platform, like other low-code application platforms, is extremely difficult to monitor for insecure configuration.
Now Microsoft releases Power Pages – the new way to build externally facing web applications in Power Platform.
The big question is – is this a mere rebranding or does it provide better security?
Evaluating Power Pages security
Zenity’s research team has taken a deep dive to evaluate the security of Power Pages. In a nutshell, the results are:
Power Pages comes with secure defaults, and even prevents some common pitfalls. However, it is still prone to misconfiguration due to lack of user oversight.
Unlike Portal Apps, Power Pages are created with Web APIs turned off. They also limit anonymous user access to the “feedback” object only.
Another positive addition is that Microsoft now blocks users from creating Power Pages in the default environment. This is a great step forward, since Power Pages can expose entire environment data to external users, and the default environment tends to be full of sensitive business data.
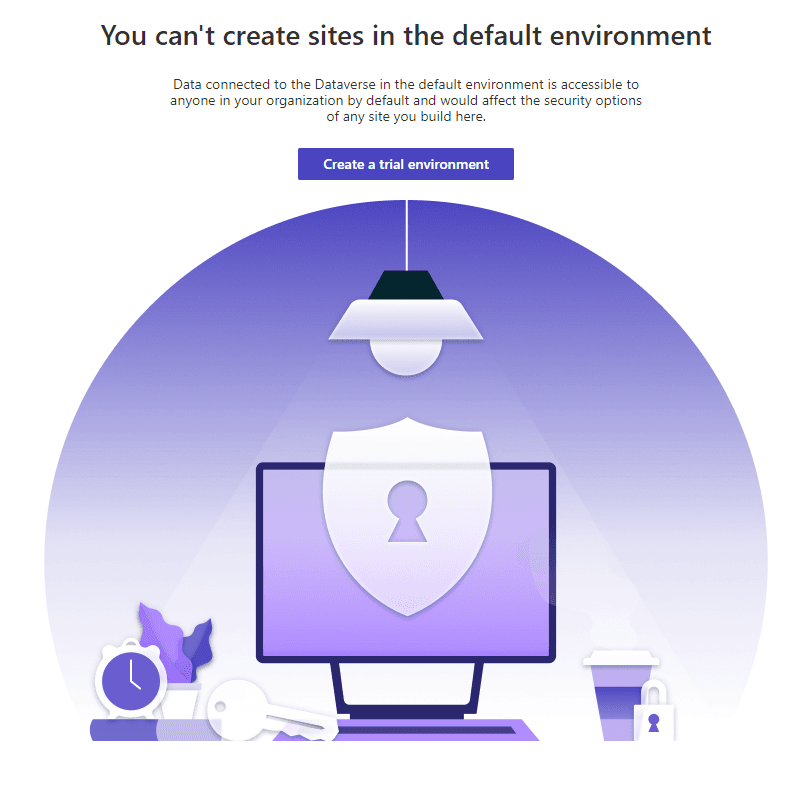
On the other hand, Power Pages still comes with default access enabled for “local users”, i.e. users outside of Azure AD. This is a significant threat vector, since these “shadow users” can easily be missed by monitoring and detection systems.
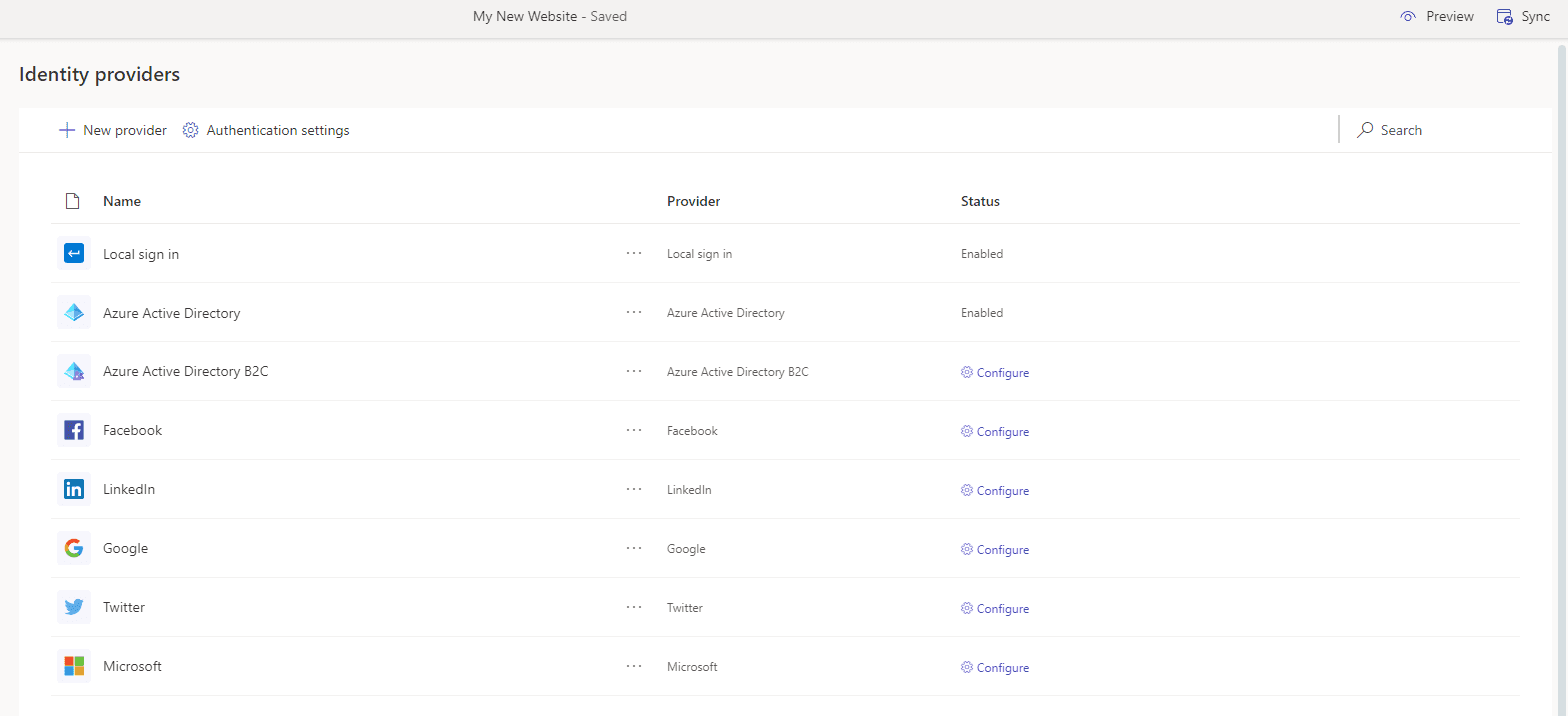
While default settings have improved, Power Pages remain prone to security issues that result from misconfiguration.
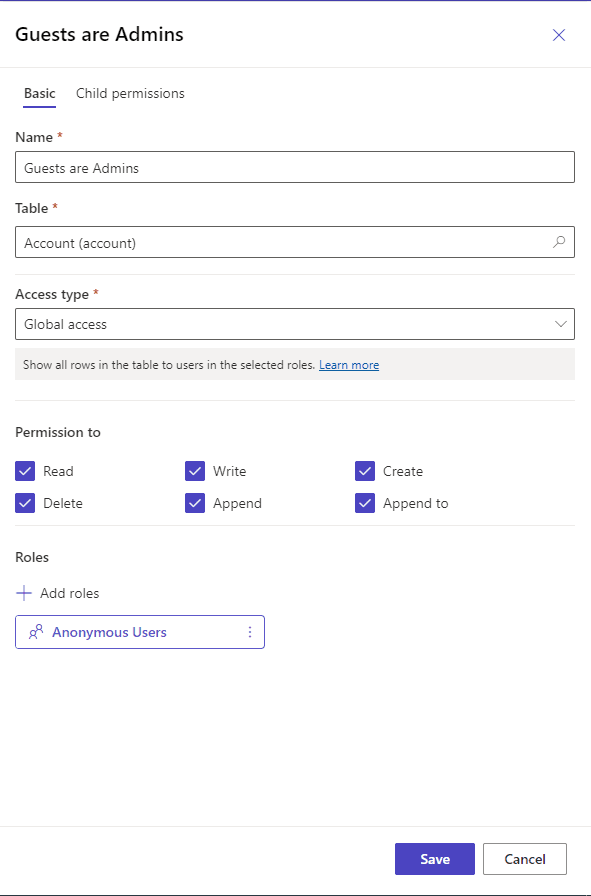
Here, for example, we set a simple table permission that elevates anonymous users to hold the same privileges as administrators have on the Account object, which typically holds customer data.
Following Microsoft’s guide, we can also re-enable the infamous Portal Apps API, and expose it for queries executed by anonymous users to https://.powerappsportals.com/_api/accounts.
The verdict
Power Pages is a great step towards security-by-default. However, it does not resolve the problem of misconfiguration. As we’ve learned from the public cloud in general and the recurring “open cloud storage buckets” issues in particular, it is the customer’s responsibility to make sure that they use the platform in a secure manner. Secure defaults are important, but are not enough on their own. and this is where Zenity comes into light providing security and governance for the newly released PowerPages.
All ArticlesRelated blog posts

The OWASP Top 10 for Agentic Applications: A Milestone for the Future of AI Security
The OWASP GenAI Security Project has officially released its Top 10 for Agentic Applications, the first industry-standard...

Inside the Agent Stack: Securing Agents in Amazon Bedrock AgentCore
In the first installment of our Inside the Agent Stack series, we examined the design and security posture of agents...

Inside the Agent Stack: Securing Azure AI Foundry-Built Agents
This blog kicks off our new series, Inside the Agent Stack, where we take you behind the scenes of today’s most...
Secure Your Agents
We’d love to chat with you about how your team can secure and govern AI Agents everywhere.
Get a Demo