RSAC 2023: A Summary
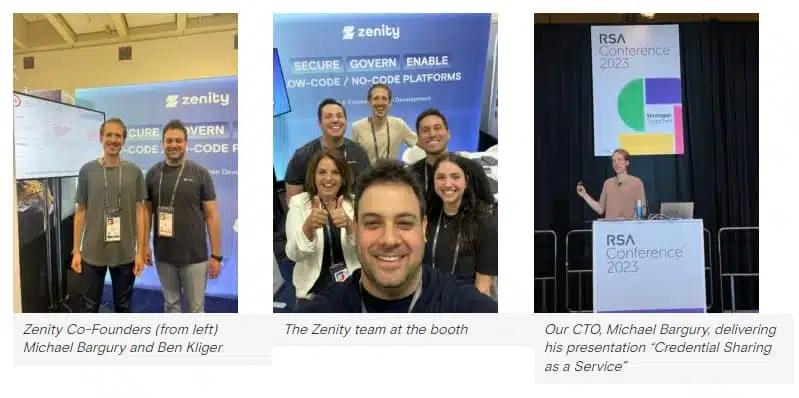
With the dust now settled and life returning to some semblance of normalcy, we’ve still been ruminating on our week in San Francisco. It was an incredible and busy week, with a lot of top notch sessions, discussions, and of course the bustling expo.



We compiled some of our daily thoughts after each full-day at the show, which you can read here, but now with some perspective, we wanted to share our four most memorable takeaways from RSA Conference 2023.
- Lack of resources and a need for speed. The name of the game remains efficiency. With macroeconomic headwinds swirling and a never-ending backlog of IT requests, organizations of all shapes and sizes are doing what they can to pool resources in an attempt to innovate. On top of this, professional developers continue to be in short supply, making it even more challenging to get things done. As such, many are proactively looking to low-code/no-code development platforms like Microsoft Power Platform, Salesforce, ServiceNow, Zapier, Appian, and others in order to enable any business user to create applications, workflows, automations, connectors, or otherwise, without needing a coding background.
- Organizations no longer have a choice for citizen development. Even for those not proactively seeking (or aware) of low-code/no-code platforms in production, citizen development is still happening, whether we like it or not. The reason being is that, at minimum, for any organization using any of these large SaaS platforms, there are low-code/no-code capabilities baked into them where people can create applications free of charge. With many free capabilities available and business users in a rush to get things done, low-code/no-code development is surging as application modernization efforts accelerate, much of it done without IT knowing, creating a shadow app development visibility problem that requires security oversight.
- Deeper understanding of what low-code/no-code development is. In conjunction with point number two, we heard from many conference-goers that they were becoming more and more familiar with low-code/no-codedevelopment. However, our main takeaway was that there are still some misconceptions about what to do from a security perspective. The best way to think about how to secure low-code/no-code development is to draw from the shared responsibility model of the cloud. Put simply, this dictates that cloud providers are responsible for the infrastructure of the cloud itself, but that end users need to secure data, applications, and more that they build using the cloud. The same goes for low-code/no-code development, where the platforms themselves will indeed provide security and governance for the platform, but not for the applications and other resources that are built by business users. This was an eye-opening discovery for many security leaders, who realize they have a blind spot as far as who is doing what, and what these resources are doing.
- Merging of AI with low-Code/no-Code. The talk of the show, naturally, was artificial intelligence. It hovered over everything, as it is clear that ChatGPT is just the tip of the iceberg and is being injected into business processes of all kinds. This is also certainly true in the world of low-code/no-code development, as software vendors make it even easier for people of all technical backgrounds to create applications, now being able to create business critical processes via text. As this attack surface explodes even further, businesses need to sharpen up their senses for how their people are using low-code/no-code development platforms and ensure that proper guardrails are in place to ensure that least privilege is implemented, and that there is comprehensive visibility for what is being created, who is creating it, how it is being used, and what data is going where.
For those with Event Access, you can catch our CTO Michael Bargury’s presentation from Thursday where he talks about how attackers have figured out ways to leverage low-code/no-code development platforms for their gain. In the presentation there are demonstrations of different attack techniques found in the wild, where low-code apps are abused during every step in the cyber kill chain. This includes the titular “Credential Sharing as a Service,” but also how phishing and ransomware attacks make their way into the world of low-code/no-code development. If you have any questions that went unanswered from the show, or would simply like to learn more, get in touch with us here!
All ArticlesRelated blog posts

Inside the Movement Defining AI Security: AI Agent Security Summit Now On-Demand
I’m still buzzing from the AI Agent Security Summit in San Francisco just a few weeks ago! From hallway discussions...
The League Assembled: Reflections from the AI Agent Security Summit
At the AI Agent Security Summit in San Francisco, some of the brightest minds in AI security and top industry leaders...

Key Takeaways for Partners from the Zenity AI Agent Security Summit
Having joined visionary leaders and top practitioners at ZenityLabs’ AI Agent Security Summit in San Francisco,...
Secure Your Agents
We’d love to chat with you about how your team can secure and govern AI Agents everywhere.
Get a Demo