Security for Autonomous Agents and Reducing Shadow AI

In the rapidly evolving field of AI, understanding the distinctions between how agentic workflows are initiated is crucial. While the verbiage among tech providers varies, it essentially comes down to whether an agent is prompted by a human from a chat interface or autonomously from external sources like emails, data changes, calendar invites, or otherwise. The inherent autonomy of all agents introduces new security risks, as agents are designed to think and act like humans, but do not have corresponding security threat models. Then, if you take it a step further, and remove the humans from even being involved in directly prompting the agent to trigger its flow of actions, it becomes an even bigger blindspot for security, governance, and trust teams.
That’s why we are so excited to introduce capabilities in the Zenity platform that provide security teams with the ability to prevent data leakage, manage prompt injection risks, and spot vulnerabilities across agents that operate autonomously without human prompting.
Introducing Autonomous Agents
Autonomous Agents not only use a more sophisticated LLM model allowing them to make more dynamic & complex decisions, but can also be triggered autonomously without needing direct human intervention. Agent Triggers are flows that can be triggered by pre-defined external events, then automatically used to prompt a specified Agent accordingly. As shown in the screenshot below, these triggers can either be pre-built…
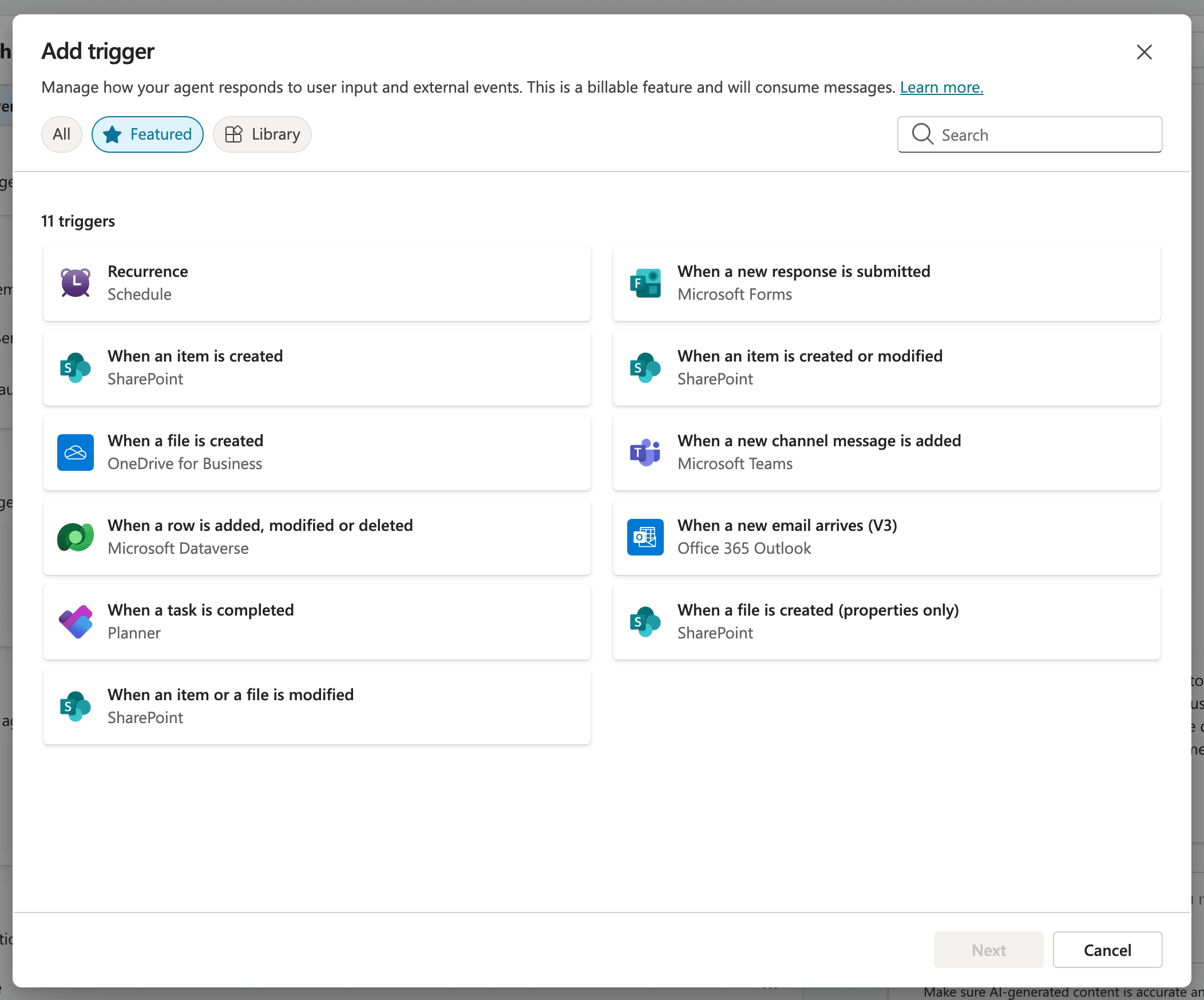
…or customized or modified, where business users can select a chosen event to generate a trigger payload to be sent back to the agent via a connector. Examples can be things like ‘when a team member is added’ and can also designate a response and/or action based on those triggers.
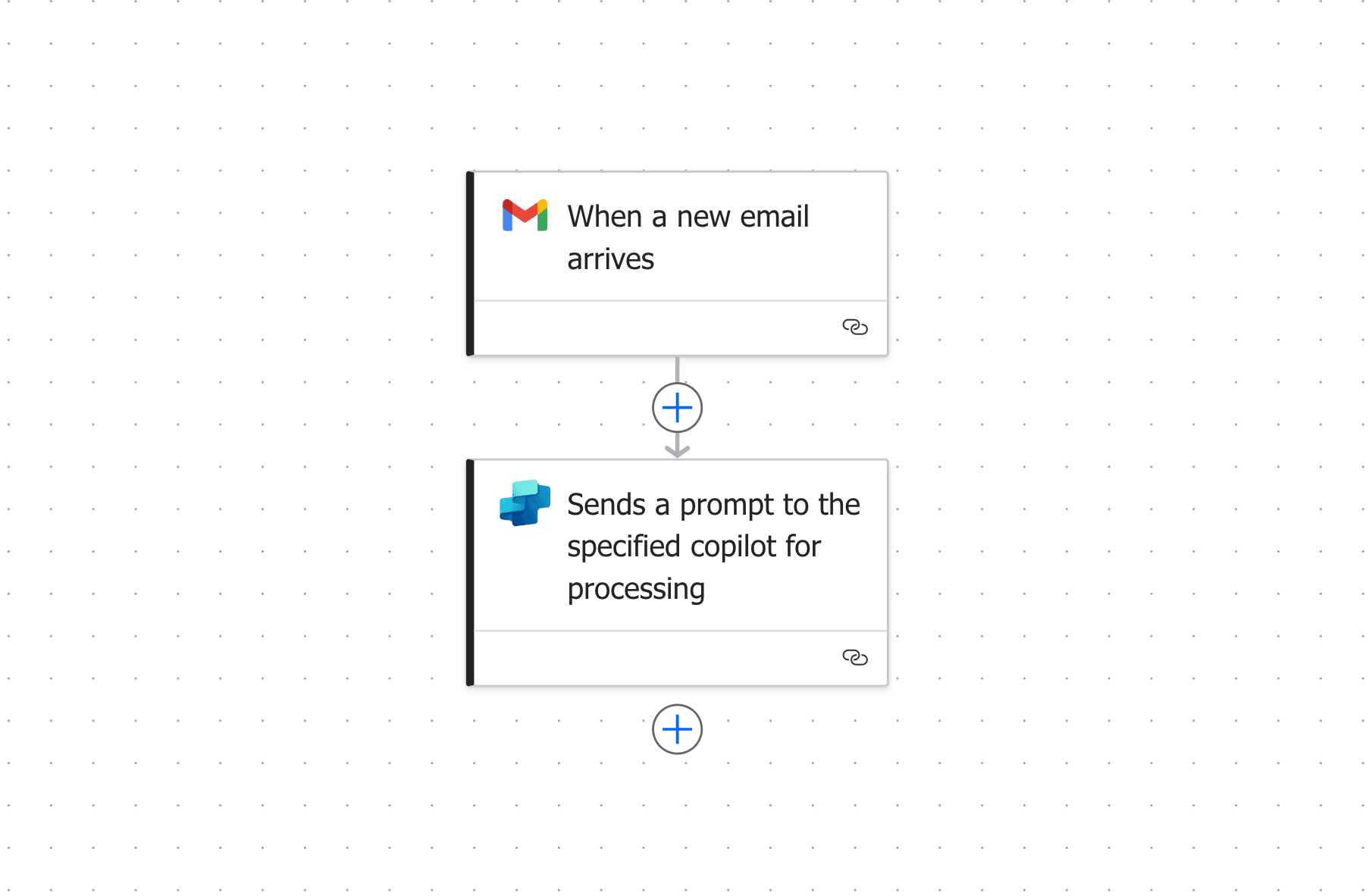
Autonomous Agent triggers are all completely implemented using drag and drop interfaces, and due to the lack of SDLC in Low-Code development, citizen developers are able to make their own choices on how to build AI Agents. This includes what guardrails to apply, who can access them, what corporate data (knowledge) they have access to, what actions they can perform, and now, what sets off their chain of actions.
With Great Power...
Agents by their nature, can and often do access highly sensitive data, as well as contain privileged and critical actionable permissions. The flexibility and proactiveness of Autonomous Agents on top of that makes them ever more vulnerable to prompt injections attacks. Triggers present new challenges from a security and governance perspective, because they open up Agents to be triggered outside of a singular chat portal, and as an example, databases can be queried and triggered using any number of commands or actions that happen in the wild, such as incoming emails.
This shift in functionality transfers the responsibility for governing agent access from the agent’s owner to the flow owner, and so many minor misconfigurations or manipulation techniques can quickly turn your Autonomous Agent into an Anonymous Agent - exposing your organization to data exposure risks as well as privileged escalation vulnerabilities.
Further, autonomous agents that can be constantly & automatically executed using Agent Triggers must be coupled with robust governance & monitoring capabilities. It’s imperative to have eyes over who can access Agents and their related resources to secure against unauthorized, underprivileged or "shadow" access to sensitive business data & privileged actions.
Comes Robust Security!
Enterprise adoption, for business users of all technical backgrounds, is at the heart of Zenity's mission of securing AI Agents everywhere. Due to the fact that Autonomous Agents are increasingly being built by citizen developers - businesses need to do their part to securely enable business users to capitalize on all the upsides of Agentic AI.
To help customers, we are proud to provide a robust AI Security Posture Management solution that will help secure both autonomous and declarative agents without compromising productivity in the process:
Observability
Zenity provides deep context into the usage of all AI Agents, whether they’re triggered by humans or not, while mapping all resources accessible to the Agent and thus providing a rich security context. Our solution can now inventory and map all agent triggers, mapping them to the agents they belong to, who created them, and what the ensuing flow looks like.
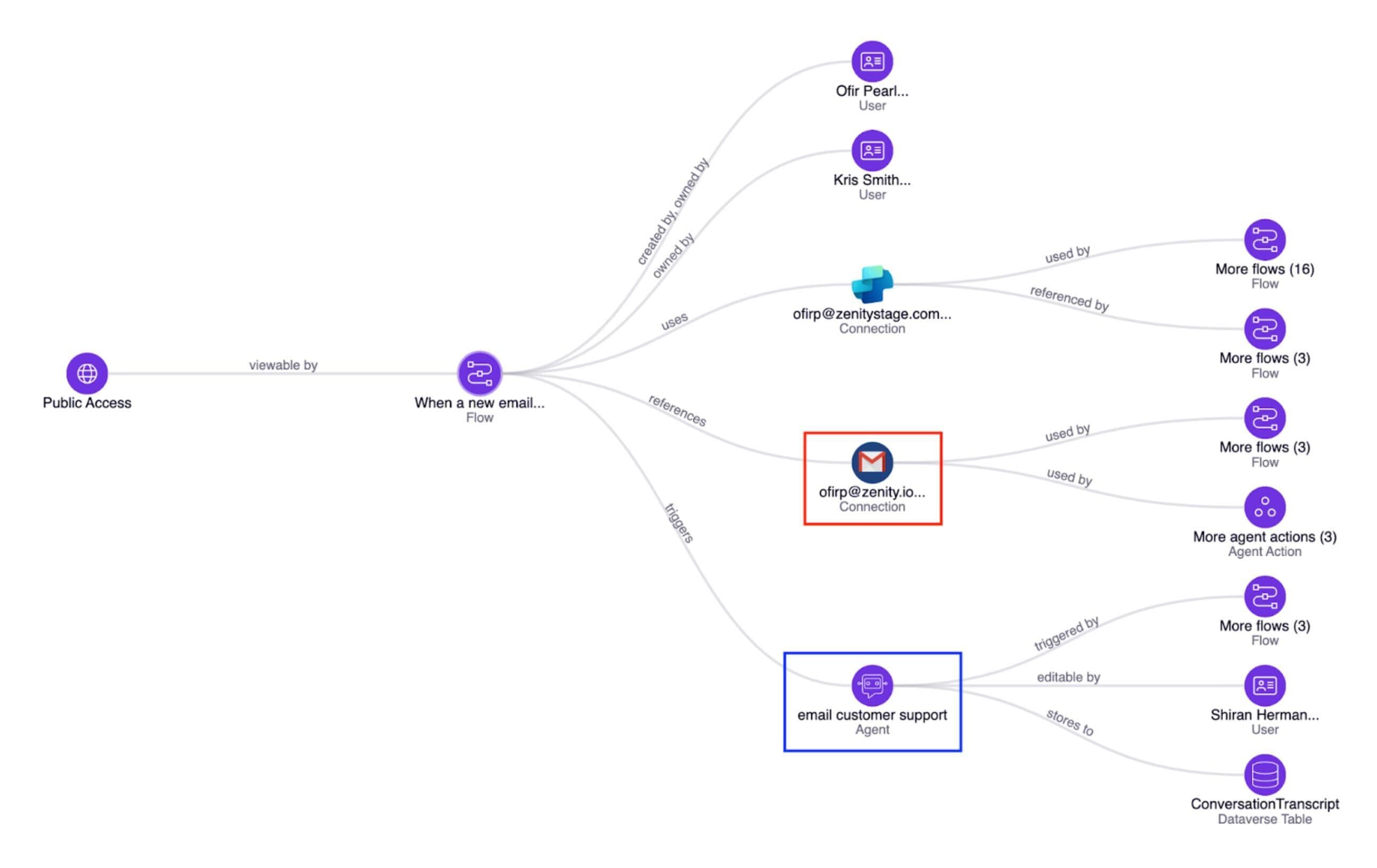
Risk Assessment
Thanks to Zenity's rich visibility & business context, we can provide advanced security threat detection for all your AI Agents, both in build-time & runtime. Zenity secures against anonymous access, shadow triggers, implicit permission sharing, and much, much more by identifying which agents are connected to sensitive data and are at risk due to shadow or risky triggers.
Governance
Using Zenity's vast automated actions offering curated to secure Agentic AI and beyond, admins can easily & quickly remediate your organization's most critical security threats. With Zenity, security teams can fire remediation actions like stopping a flow that is exposed to anonymous user manipulation or isolating flows that have embedded user credentials.
As we continue to navigate this new frontier of AI-enhanced productivity, we believe the key to success lies in striking the right balance between innovation and security. With the right approach and tools, organizations can unlock the full potential of Agentic AI while keeping their data, systems, and users safe.
Conclusion
Autonomous Agents bring the age of Agentic AI straight to citizen developers and out into the wild. While the technical differences might be subtle between autonomous and declarative agents, the meaning behind them is monumental! Agents are no longer only accessible in chat, but rather can be powerful & intelligent automation tools that can utilize privileged capabilities & business data in dynamic and independent ways.
However, with the ease of Low-Code/No-Code development and the powerful integration of Autonomous Agents into your organization’s business data & assets, there are big risks that need to be accounted for in order to properly govern the usage of Autonomous Agents from end-to-end.
Embrace the future of AI and unlock new levels of productivity, efficiency, and innovation with Zenity’s AISPM capabilities that extend into any other AI Agents that business users are building and customizing. Dive head first into the secured future of AI! Book a demo today.
All ArticlesRelated blog posts

GreyNoise Findings: What This Means for AI Security
GreyNoise Findings: What This Means for AI Security Late last week, GreyNoise published one of the clearest signals...

The CISO Checklist for the New AI Agent Reality
AI agents are now acting across SaaS, cloud, and endpoint environments with identities and permissions that traditional...
Demystifying AI Agent Security
Let me be the first to say it, this space - AI agent security and governance - can be confusing. When I joined...
Secure Your Agents
We’d love to chat with you about how your team can secure and govern AI Agents everywhere.
Get a Demo