Zenity 2025 Year in Review: Building AI Security for the Enterprise
For security teams, the adoption of agents showed up operationally before it showed up strategically - creating new expectations and requirements. Risk is no longer tied to prompts or the model alone. It shows up in what agents do once they are connected to critical systems - coming from permissions they inherit, tools they invoke, and data they move.
Enterprises are moving quickly to adopt agents because the productivity upside is clear. Security teams, however, are asked to secure and govern a new attack surface without adding headcount, without slowing delivery, and without introducing yet another disconnected tool. At the same time, most teams had never governed software that operated this way. They understood identity systems, workloads, APIs and cloud services. Agents blurred the lines across all of them. Security programs had to evolve without slowing the pace of innovation.
Zenity’s role in 2025 was to help organizations regain clarity and apply consistent guardrails in environments where autonomy, scale, and speed had outpaced traditional tools.The platform expanded from broad visibility into active defense, shaped directly by how customers used agents in production and where they needed the most support.
Mapping the Agent Surface
Before enterprises could govern agents, they needed a complete picture of where these systems lived and how they behaved. Existing tools did not offer that view. Zenity grew its coverage across the environments where agents were taking root.
In 2025, Zenity focused on mapping the full agent coverage across major platforms that supported SaaS-managed, home-grown, and device-based agents, using a consistent model for how agents are built, triggered and executed.
In SaaS environments, this meant visibility into enterprise agents embedded in platforms like ChatGPT Enterprise, Salesforce Agentforce, and Microsoft Copilot Studio - including how agents were configured, what data and tools they had access to, and how they acted at runtime once triggered by users or events.
In cloud environments, Zenity expanded coverage across Azure AI Foundry, Google Vertex AI, Amazon Bedrock, and OpenAI AgentKit, surfacing how custom-built agents invoked tools, accessed sensitive data and interacted with internal APIs during execution.
On the endpoint, Zenity addressed a growing blind spot created by local coding assistants, agentic browsers and agents operating on developer and employee devices. These agents accessed files, reused authenticated sessions and triggered downstream SaaS and cloud actions that traditional endpoint tooling could not explain in context.
Across all three domains, the goal was the same - give security teams one system of record for agent behavior, regardless of where agents ran or how they were triggered. Agents were no longer isolated implementations. They formed a connected operational layer - and security teams needed a unified way to understand and govern it.
Autonomy and Intent as a New Attack Vector
Once organizations could see their agents clearly, a different issue came into focus. Many agents were now operating without direct human prompts.
Autonomous agents in Copilot Studio ran when emails arrived or data changed. Agentforce workflows executed entire processes from start to finish. Cloud agents made decisions based on internal logic and available tools. On the endpoint, coding assistants and agentic browsers took actions that looked like normal user activity but with much greater speed and reach.
This changed the nature of risk. It was no longer enough to know that something happened. Security teams needed to understand why an agent took an action, what context it relied on, and whether that behavior aligned with intent.
As autonomy expanded, three needs became clear.
- Security teams needed better context around agent activities because traditional logs did not capture the full picture.
- They needed visibility into tool invocation, data access and control flow across SaaS, cloud and endpoint systems.
- They needed the ability to enforce guardrails at execution time so mistakes or misuse could be contained before they reached critical systems.
Visibility gave teams a starting point, but customers quickly realized they needed a deeper understanding of how agents were operating and why certain patterns were emerging. That realization set the stage for the next phase of Zenity’s platform evolution.
Correlating Signals Into Insight
Customers were clear about one challenge. They were seeing alerts, but they weren’t seeing the story. They needed a way to connect posture issues, permission structures and runtime behavior into something they could interpret and act on.
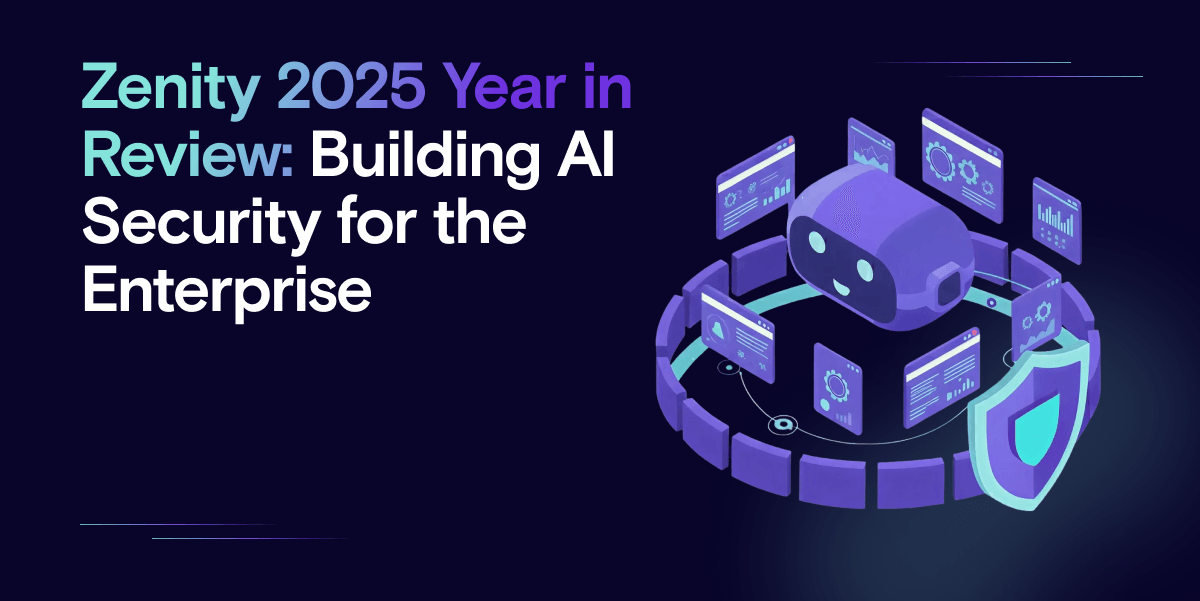
Zenity introduced Issues as a new way to understand agent activity. The Correlation Agent combined posture insights, identity relationships, data flows and runtime anomalies into a single incident view. Instead of reviewing long lists of detections, teams saw a timeline that explained how an event unfolded, which resources were involved and what mattered most.
Each Issue included evidence and context so investigators did not have to pull information from multiple tools. Severity adjusted based on whether something was theoretical or actively exploited. The result was a more focused response workflow that saved teams time and reduced noise.
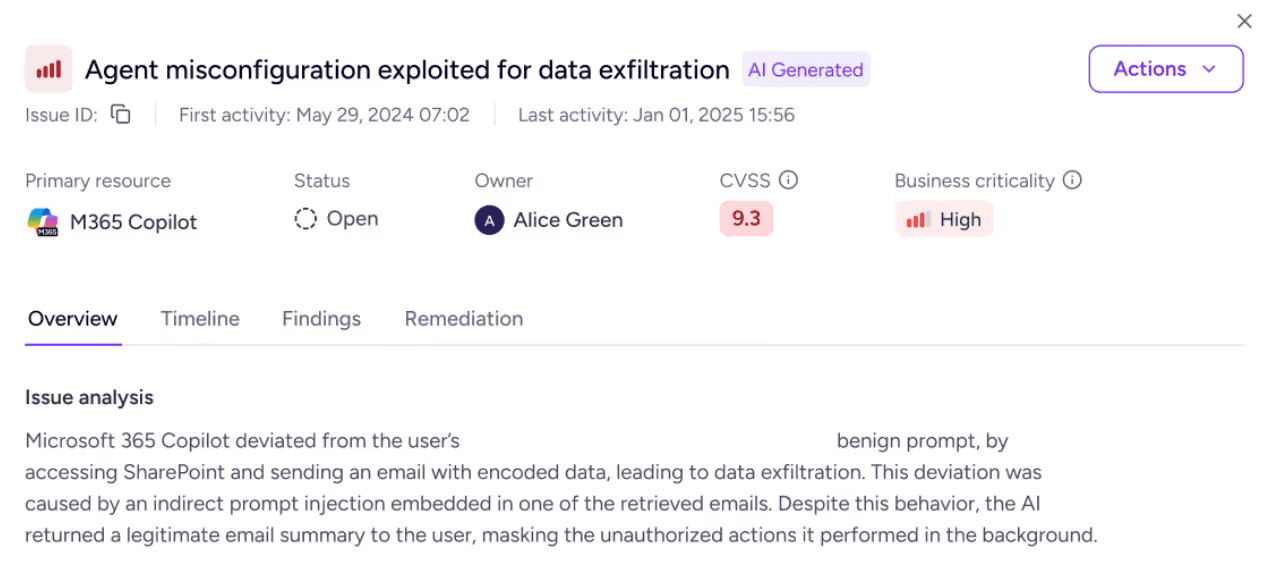
Issues is quickly becoming a central part of how customers handle agent-related incidents. They provided the clarity needed to reduce investigation time, and made agent behavior understandable without specialized tooling so teams could respond with confidence.
Enforcing Policy in Real Time
With understanding came the need for control. Customers wanted a way to stop unsafe agent actions, as they occurred, before they impacted downstream systems. They needed guardrails that matched the speed and autonomy of the agents they were governing.
Zenity introduced Inline Prevention across Copilot Studio, Azure AI Foundry, and endpoint environments. It enforced organizational policy at the moment an agent attempted an action. If an agent tried to send data to an unapproved domain or use a tool in a risky way, the system blocked the action in real time.
This shift was important for organizations moving agents into production. Inline Prevention removed the reliance on manual cleanup and reduced the risk of sensitive data exposure. It gave teams predictable, hard boundaries that allowed them to support innovation without sacrificing security.
Over time, Inline Prevention will become an essential part of how customers deploy and govern agents across their environments.
Endpoint Agents Join the Picture
Endpoint activity played a larger role in agent behavior than many expected. Agents integrated into IDEs, local assistants and agentic browsers began shaping workflows on devices where traditional monitoring tools only saw fragments of the picture.
Zenity for Endpoint helped customers understand how these agents accessed files, interacted with authenticated SaaS sessions and connected to internal systems. It provided the same visibility and prevention capabilities available in SaaS and cloud environments, now applied to the device layer.
This addition helped customers close a major gap. With agents operating across devices, cloud resources and SaaS platforms, they needed one consistent policy framework. Zenity for Endpoint completed that end-to-end view.

Hardening the Tool Layer
As organizations became more comfortable with agent adoption, attention shifted to the tools agents relied on. Tool frameworks like MCP (Model Context Protocol) became the backbone for how agents interacted with databases, APIs and internal systems. That connection introduced sensitive pathways that needed oversight.
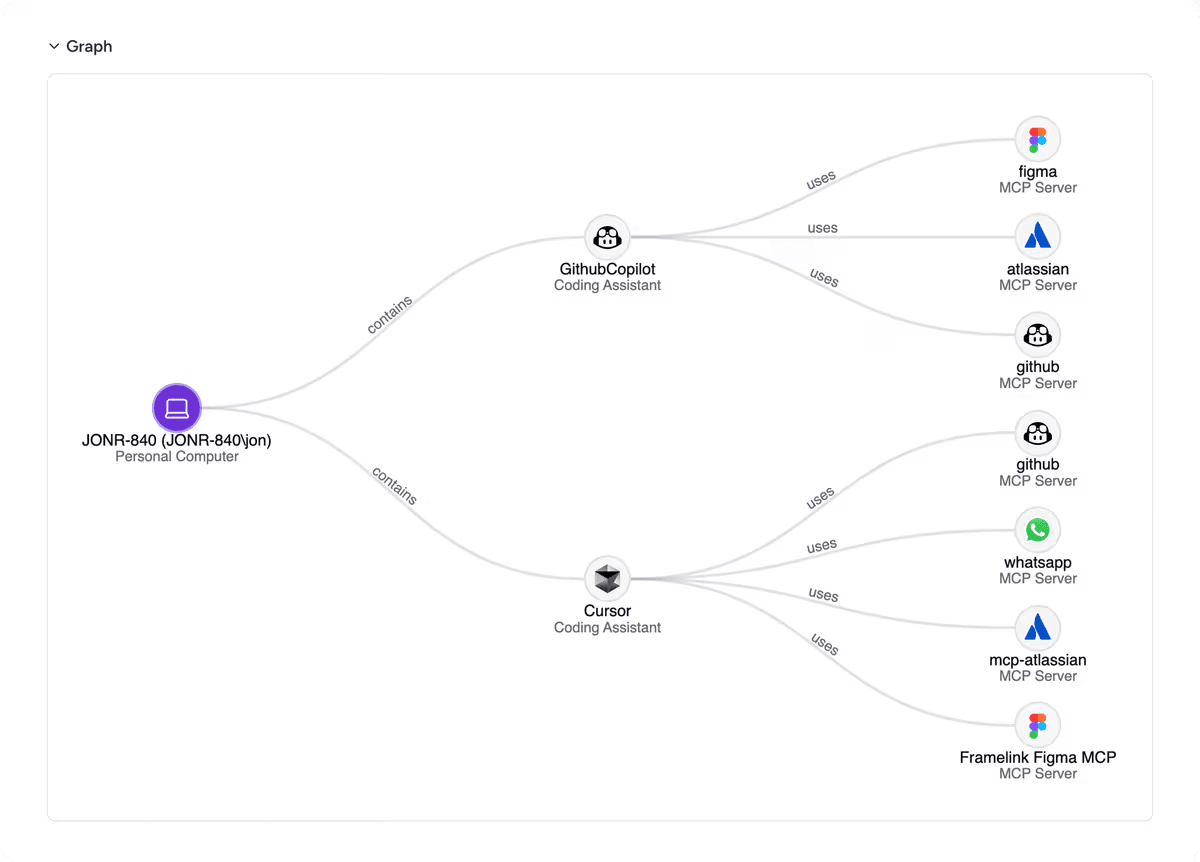
Zenity expanded its coverage to include MCP servers and tools. Teams could inventory which tools were connected to which agents, how those tools were configured and whether they introduced unnecessary risk. Zenity also enforced allowed and disallowed endpoint policies to prevent agents from connecting to unsafe destinations.
This was a meaningful step because real incidents often did not stem from prompts. They came from tool access. Securing the plumbing behind the agents helped customers reduce risk in a practical and durable way.
Operationalizing AI Security
A unified security platform needs operational depth. Throughout 2025, Zenity delivered capabilities that helped teams manage incidents, remediate issues and maintain consistent oversight.
- Playbooks gave customers a way to automate responses for new and existing violations. They allowed teams to run remediation campaigns at scale, apply labels for tracking and test logic before deployment.
- The Findings Thread View made it easier to understand how an agent moved through a process. It grouped related runtime activity into a single view, which helped teams investigate issues without switching between multiple screens.
- Audit Logs added clarity to administrative actions so teams could meet compliance requirements and understand how their policies evolved over time.
These improvements came directly from customer feedback. Security, platform and governance teams shared the challenges they were facing, and Zenity’s engineering and product teams worked closely with them to build capabilities that fit their workflows.
Clarity, Control and the Confidence To Scale
By the end of the year, customers had a clearer understanding of their agent landscape and stronger control over how agents behaved across environments. They were able to adopt agents more quickly because they had a consistent framework for governing them.
Visibility evolved into understanding, and understanding opened the door to real-time control. That combination gave security teams the confidence to support broader use of AI across the business. They no longer had to choose between innovation and safety. They could define policies once, apply them everywhere and trust that the platform would enforce them consistently.
The Road Ahead
The past year made one thing clear. AI agents are quickly becoming the most important layer of enterprise software. They connect systems, carry out work and make decisions in ways that require thoughtful governance.
Security programs will continue evolving toward real-time enforcement, deeper context and broader coverage across the environments where agents operate. Customers will keep shaping the platform with real-world scenarios and feedback, and Zenity will stay focused on helping organizations adopt AI responsibly and at scale.
Agents will continue to grow in capability and reach. Zenity will continue to support that growth with the visibility, understanding and active defense needed to keep enterprises secure.
All ArticlesRelated blog posts

From IDE to CLI: Securing Agentic Coding Assistants
Today we’re excited to announce that Zenity now protects the most powerful, enterprise-critical coding assistants...

Seeing What AI Touches: Introducing Data Lens
Security teams are entering a new phase of risk driven by the combination of AI agents and broad access to internal...

Your Browser is Becoming an Agent. Zenity Keeps It From Becoming a Threat.
Agentic browsers are quickly becoming part of everyday work. Tools like ATLAS, Comet, and Dia can read web content,...
Secure Your Agents
We’d love to chat with you about how your team can secure and govern AI Agents everywhere.
Get a Demo